Malware authors have taken aim at mobile devices, Android in particular, and they are relentless in their search for vulnerabilities and new ways to trick users into installing malicious apps.
Security researchers are not wasting time either, and constantly come up with more or less permanent defensive solutions; but the best way to protect against threats of any kind is security awareness.
Based on this belief, researchers at Bluebox created Trustable, a free Android app that evaluates the security risks posed by software available on the device.
Bluebox is a mobile data security company credited for discovering two highly significant flaws in the Android operating system, Master Key and the more recent FakeID.
Scanning is fast, shows active vulnerabilities
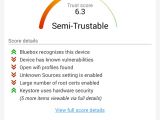
The principle behind Trustable is simple: it scans the mobile device and the apps on it, and provides a score reflecting the trust level based on permissions granted, unpatched vulnerabilities and insecure system settings.
The rating goes from 0.0 to 10.0, a lower score meaning that the device is below average as far as security is concerned, and as such, it is not to be trusted. The numbers can change in time, depending on the actions taken by the user to increase or lower security.
“As of October 2014, the Google Play developer console indicates there are over 6,900 different Android devices actively utilizing the Google Play store,” Bluebox says, each of them bringing to the table different security approaches.
The scanning process takes little time to complete and the results are broken into three sections that provide general information about the state of the device, vulnerabilities detected, and the apps with permissions that could have an impact on the trustability of the Android.
As far as vulnerabilities are concerned, apart from Master Key and FakeID, also detected are Heartbleed and Linux Futex (Towelroot).
Patches exist for them, but pushing them to the clients depends on the manufacturer of the phone, as well as the carrier.
Apps with risky permissions are revealed
The more interesting part is the one touching on the applications installed and their permissions. Trustable offers information about the number of trust certificates available and privileges apps have in order to function.
These include dangerous-level permissions, which could cost the user money, corrupt data or access personal information, as well as allow placing phone calls, reading and sending text messages or reading the list of contacts.
Removing the items posing a security risk would lead to an improved score, but achieving and maintaining a perfect one is not an easy task, and it does not depend entirely on the user.
Multiple components influence the score, including user profile
“Trustable by Bluebox measures a variety of signals on the device to arrive at the trust score. We provide guidance for users of devices to help maximize the score for their device,” said via email Andrew Blaich, lead security analyst at Bluebox Security.
A perfect score takes into consideration things like support for SELinux (security-enhanced Linux), which is an access control security mechanism, device encryption, passcode locks, enabled roots of trust, or vulnerabilities. All these depend both on the device and the manufacturer.
In the case of vulnerabilities, users have no control over implementing them, and they have to wait for a patch to become available and then be distributed in order to increase the trustability rating of the device.
When asked about apps that present a risk but are beneficial from a productivity perspective, Blaich said that “only the apps that are permitted to do risky behavior are counted” and that more trustworthy alternatives should be sought, for a better score from Trustable.
The newly launched Bluebox app is flexible enough as to consider multiple user profiles, recognizing customization needs such as rooting the device or running variations of the operating system for better performance and security.
This obviously has an impact on the final score from Trustable. Allowing root or full system access is flagged as a concerning matter for less advanced users, while in the case of experts, it does not affect the rating since this state is expected.

 14 DAY TRIAL //
14 DAY TRIAL //