Multiple websites part of a phishing operation targeting PayPal users have been taken offline after a security company detected the registration of domains that hosted pages looking almost identical with those of the e-commerce service.
Some of the fraudulent websites had been used in the past, with one of them, dormant since 2005, being re-registered on January 22, 2015.
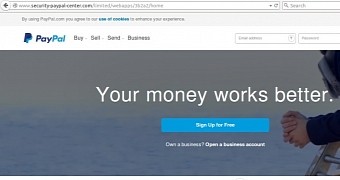
Phishing locations are almost indistinguishable from the original
OpenDNS Security Labs, a company that includes suspicious domain registration in its activities, says that the pages hosted by the malicious domains were “virtually indistinguishable from the legitimate PayPal.com site.”
Apart from this, the fraudsters relied on domain names that could pass as belonging to PayPal for an untrained eye. By combining these two elements, the cybercriminals could fool a large amount of users into disclosing credential sets.
In a blog post on Wednesday, the company listed x-paypal[.]com, redirectly-paypal[.]com, securitycheck-paypal[.]com, security-paypal-center[.]com and paypalinspection[.]com as examples, saying that many more were discovered.
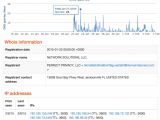
During the investigation, the researchers observed the DNS queries made to two of the fraudulent locations, which in one case spiked to 24 on January 23 and in the other a significant increase to 38 queries was noted on February 4.
According to OpenDNS, the nameservers of redirectly-paypal[.]com pointed to Wix.com since January 25 but it could have been registered at an earlier time and then transferred to Wix’s service.
Some of the fake websites were registered with Enom, a domain registrar that popped up in numerous instances during the investigation of typo-squatting domains.
Detected sites have been blocked by OpenDNS
OpenDNS reported the fraudulent addresses to PayPal who responded that the fraud and abuse department was on the case and initiated the procedures for removing the websites.
“In the meantime, OpenDNS has blocked access to these domains for all users of our DNS infrastructure,” the company said.
Phishing is extremely common and web browsers protect users from landing on fraudulent pages. Most of the time, cybercriminals have a short operational window before the sites are detected and blocked, but in this case the fraud persisted for a longer period of time due to the convincing appearance of the pages.
Among the clues revealing the fraud is lack of a secure connection (HTTPS), which is enabled for most log-in pages online.
 14 DAY TRIAL //
14 DAY TRIAL // 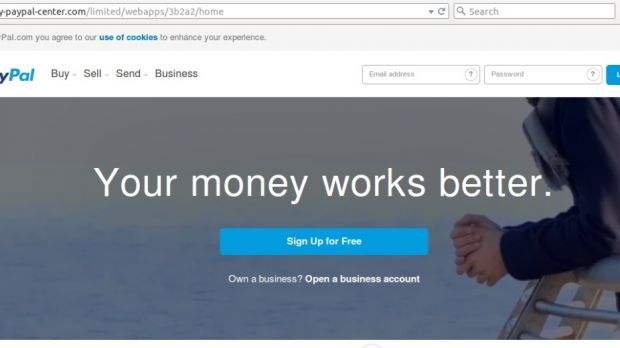
![DNS queries for security-paypal-center[.]com](https://news-cdn.softpedia.com/images/newsrsz/Flurry-of-PayPal-Phishing-Sites-Taken-Down-473076-3.jpg)