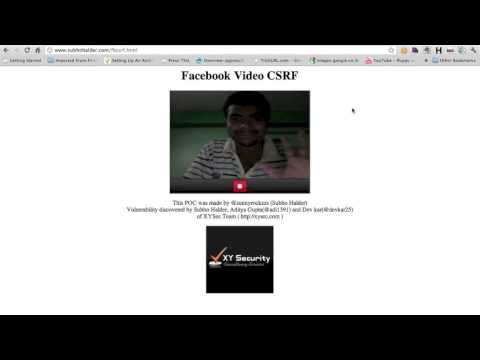
XYSEC Labs security researchers Subho Halder and Aditya Gupta have identified a Cross Site Request Forgery (CSRF) vulnerability in Facebook.
To demonstrate how an attacker could exploit this security hole, the experts made a proof-of-concept video. They showed that a cybercriminal could record a video of the targeted user via his/her own webcam and seamlessly post in on their Facebook timeline.
“This is an classic example of a Cross Site Request Forgery(CSRF/XSRF), a kind of security attacks in which the actual source from which the request is being made, is not being properly verified. So, in our case, Facebook wasn't able to judge whether an attacker is making the request of posting the video as a status, or it was Facebook itself,” Gupta told Softpedia.
He explained that for this type of attack to work, the victims need to be logged in to their accounts.
Posting a video recorded with the user’s webcam is just one example, which requires some degree of interaction from the victim, but the CSRF vulnerability could be leveraged in other ways as well.
“There could be other attack vectors as well using this vulnerability, in which a video (from other source, not the webcam) could be posted to his timeline, without any kind of user interaction,” the expert noted.
The researchers notified Facebook of the flaw. Initially, the social media network told them that it was not a serious security hole, but after the experts provided them with the proof-of-concept that demonstrated how it could be exploited, they agreed that it was serious and rushed to fix it.
“We were expecting a bounty of $500, because that is the usual amount facebook pays to security researchers, unless it is a serious issue. But facebook said that it would be paying us $2500 for this one. This came more like a Christmas present for us, from Facebook,” Gupta said.
Here is the POC video made available by the experts:
 14 DAY TRIAL //
14 DAY TRIAL //