The FlashPack exploit kit is currently delivered to the systems of unsuspecting users in Japan through a script that publishes social media sharing buttons on websites.
The ready-made script is available on a website promoting the social media add-on, and administrators only have to integrate it into their site to have the buttons loaded.
However, researchers at Trend Micro have observed that this script is used for malicious purposes, as on some websites it directs the user to the FlashPack script.
As its name clearly suggests, the kit delivers Flash exploits to the victim, causing malware to be downloaded on their systems.
Fraud researcher Joseph Chen from Trend Micro says that among the vulnerabilities leveraged is CVE-2014-0497, which allows attackers to remotely execute arbitrary code; the security flaw was addressed in February, but not all users updated their Flash Player, running the risk of becoming victims of cyber attacks.
Chen notes that in one specific case they saw the Carberp Trojan being delivered to victims, whose source code was leaked on underground forums.
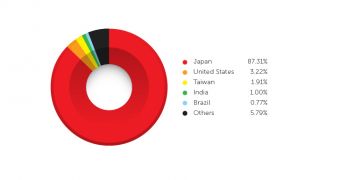
Most of the targets seem to be from Japan, as the country accounts for 87.31% of the infections, according to Trend Micro telemetry data. Next is the United States, with 3.22%, and Taiwan, with 1.91%.
“Site owners should be very cautious about adding add-ons to their site that rely on externally hosted scripts. As shown in this attack, they are trivial to use in malicious activities. In addition, they can slow the site down as well. Alternatives that host the script on the same server as the site itself are preferable,” said Chen in a blog post.
 14 DAY TRIAL //
14 DAY TRIAL //