These days, the 2013 edition of the DefCamp security conference is taking place in Bucharest. There have been a lot of interesting presentations so far. One of the researchers presenting his findings at the event is Bogdan Alecu, who specializes in mobile security.
Alecu has found a vulnerability in Google devices that can be exploited to cause them to reboot. The security hole impacts devices such as Galaxy Nexus, Nexus 4 and Nexus 5, regardless of the version of Android they’re running (even the latest KitKat), as long as they have the official ROM.
Tests have been made on non-Google devices, including Samsung and HTC, but they don’t appear to be impacted.
So how does the attack work?
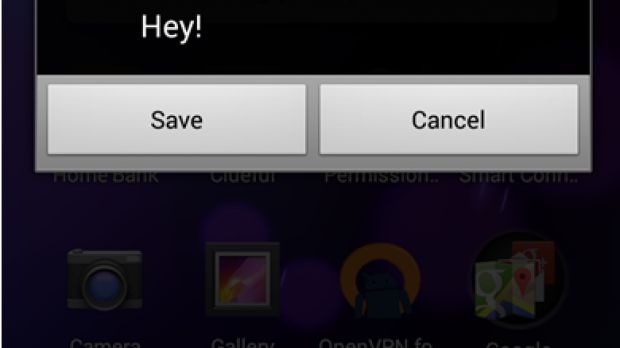
The attack is related to Class 0 (Flash SMS) messages. Flash SMS messages are the types of messages that are displayed on the device’s screen as soon as they’re received. They’re often used by mobile operators to send messages to customers.
Only one such message can be received at a time and if it’s not saved by the user, it will disappear.
The expert has noticed that whenever Google devices receive such a message, an extra layer is added on the screen and the background turns darker. He wanted to test if sending multiple messages to a device, at short intervals, would make the background completely black. He also wanted to check if this would result in a memory leak.
Based on Alecu’s experiments, the screen does go black. In fact, in most cases, if 30 Flash messages are sent at a 1-second interval, the device reboots. This can also lead to a memory leak.
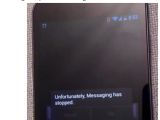
In other scenarios, when a large number of messages are sent, the messaging application stops working, or the mobile network communication process is restarted. In the latter case, since the device cannot connect to the Access Point Name (APN) any more, it can no longer use mobile Internet.
In a plausible scenario, the attacker sends messages to his victims in an attempt to cause their devices to reboot. Since most users protect their phones with a PIN, mobile connectivity is lost until the victim notices that the device has rebooted and enters the passcode.
For instance, such a denial-of-service attack could be useful for cybercriminals who want to make fraudulent bank transfers and want to prevent the victims for receiving fraud alert messages on their phones.
The researcher notified Google’s Android Security Team over 1 year ago, but so far the vulnerability has remained unpatched. In July, someone at Google told the expert that a fix would be implemented in Android 4.3. However, it wasn’t.
In the meantime, Alecu has teamed up with Michael Mueller (c0rnholio) to develop an application that protects devices from such attacks. The app, called Class0Firewall, is available for free on Google Play.
Check out the proof-of-concept videos published by the researcher:
 14 DAY TRIAL //
14 DAY TRIAL //