A bug in old releases of the Adobe Flex SDK compiler, patched by the company in 2011, can still be leveraged by an attacker against the latest versions of Flash Player browser plug-in, security researchers have discovered.
The flaw, identified as CVE-2011-2461, is a same-origin bypass (SOP) and allows injection of arbitrary scripts or HTML code from unauthorized sources.
Popular websites host vulnerable SWFs
Luca Carettoni from LinkedIn’s security division and Mauro Gentile, researcher at Minded Security, discovered that all applications built with a version of Flex vulnerable to the glitch ( 3.x and 4.x before 4.6) can still be exploited.
These are SWF files that are loaded by the latest versions of Flash, making the bug exploitable in the current context. As such, they need to be either recompiled with a more recent edition of the SDK or patched.
The duo says that, during their research, a wide analysis was conducted to identify vulnerable SWFs hosted on popular websites, using a custom tool that detected code patterns associated with this glitch.
The results showed that a large number of websites were affected, three of them being included in Alexa’s Top 10.
The utility used by the two researchers is available for download; called ParrotNG, it is a command line tool and Burp Pro Passive Scanner plug-in.
Flaw has serious security risks
“This vulnerability allows attackers to steal victims' data (via Same-Origin Request Forgery), or perform actions on behalf of the victim (via Cross-Site Request Forgery), by asking them to visit a malicious web page,” the two researchers explain in a blog post.
Among the risks involved there is forcing a Flash movie to run same-origin requests and deliver the replies to the attacker.
“Since HTTP requests contain cookies and are issued from the victim’s domain, HTTP responses may contain private information including anti-CSRF tokens and user's data,” and this can happen regardless if the web browser or the Flash plug-in are fully patched, they say in the post.
The weakness has been privately disclosed in the past months to the owners of some of the largest websites, but warning all impacted entities is difficult this way. That’s why Carettoni and Gentile took the decision to publicly disclose the technical details.
Their recommendation is to recompile the Adobe SWF files (static libraries included) using the latest SDK version available or to patch them with the official Adobe patch tool. A third option would be to delete them completely.
Slides with details of the research are embedded below:
The old is new, again. CVE-2011-2461 is back! from ikkisoft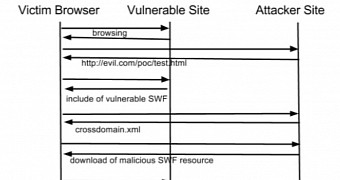
 14 DAY TRIAL //
14 DAY TRIAL //