Cybercriminals have been running a new campaign that aims at changing the domain name system (DNS) settings in order to point to malicious servers hosting Fareit malware; the threat masquerades as an update for the “Pro” version of Flash Player.
With the DNS configuration modified this way, victims can no longer reach legitimate websites and land instead on pages controlled by the attacker. The risk is severe because the domain name in the web browser is the correct one, making it appear that any content presented comes from a legitimate source.
DNS servers are responsible for resolving the connections to the right website by translating the domain name into the IP address of the legitimate machine serving the content. By altering the IP list, the connection is established to a different server, while the domain name in the web browser remains unchanged.
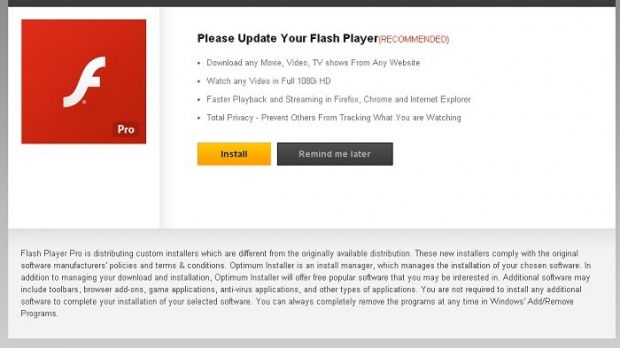
An update for Flash Player “Pro” is highly suspicious
A “Pro” version for Flash Player does not exist and being asked to update it should be a clear indication of malicious activity.
However, since the file appears to be delivered by the website the users try to visit, many would fall for the trick and infect their computer with Fareit; notice in the first image below that the update request appears to come from google.com, when in fact it is foisted by a rogue machine.
The capabilities of the malware include stealing credentials for different types of accounts, from crypto-currency wallets to passwords stored in the web browser. It can also be used to funnel in other malicious software that have a different purpose (ransomware, financial banking).
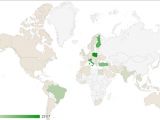
Most of the infections have been recorded in Poland
Security researchers at F-Secure observed that the malware piece in the recent campaign was delivered from servers located in Turkey, Germany, Netherlands and the US. As per the information from the security company, multiple DNS servers making the connections are located in Canada.
Most of the Fareit infections have been traced to computers in Poland, although users in Brazil, Italy, Finland and Turkey are also affected.
If the DNS server settings have been altered, security experts advise restoring them on the router either by resetting the device or by manually entering the correct addresses. Changing the router password and turning off remote administration are also among the recommended actions.
On the desktop, the DNS cache should be flushed either through a reboot or running the ipconfig /flushdns command. Then, an antivirus scan with an updated, reputed solution should be carried out.
 14 DAY TRIAL //
14 DAY TRIAL //