Adobe started to push a new release of Flash Player that fixes the zero-day vulnerability currently exploited in the wild and reported by the company on Monday.
Identified as CVE-2015-0313, the glitch has been leveraged by attackers through the Hanjuan exploit kit in malvertising campaigns on popular websites such as DailyMotion.
Reported by Peter Pi from Trend Micro, the vulnerability is exploited by cybercriminals against users relying on Internet Explorer and Mozilla Firefox for web navigation, regardless of the underlying Windows operating system version.
Security researchers at Trustwave have analyzed the zero-day vulnerability and concluded that it is a use-after-free “caused by a bug in how Flash handles the FlashCC (previously Flash Alchemy) ‘fast memory access’ feature (domainMemory), when the last is used by flash Workers (Flash threads).”
The flaw affects Flash Player 16.0.0.296 and earlier versions for Windows and Macintosh, as well as build 13.0.0.264 and earlier 13.x. versions of the application.
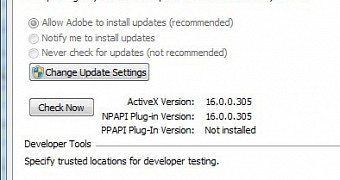
On Wednesday, Adobe updated the initial security bulletin for CVE-2015-0313, announcing that the new revision (16.0.0.305) would be delivered automatically on desktop runtime edition where the auto-update mechanism is turned on.
The company expects that a manual download will become available on Thursday so that all users can install the latest revision and mitigate the risk.
The plug-ins for Internet Explorer 10 and 11, and Google Chrome will be delivered automatically through the appropriate mechanisms of the web browsers.
[UPDATE]: The download for the desktop runtime version of Flash Player 16.0.0.305 is currently available from Adobe's servers. The latest version of Flash Player can be downloaded from Softpedia for Windows and Mac.
 14 DAY TRIAL //
14 DAY TRIAL //