Kaspersky has partnered up with CERT-Bund (Computer Emergency Response Team für Bundesbehörden), Symantec and ITU-IMPACT in an effort to further analyze the now-infamous malware known as Flame. More precisely, the researchers studied the threat’s command and control (C&C) servers.
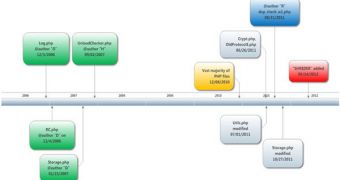
First of all, they learned that the development of the platform C&C code may have started as early as December 2006, which means that the platform is much older than initially estimated.
They believe that a four-man team developed the C&C, one of them – whom they dubbed H – most likely being the lead developer, since he implemented some “smart patches” and “complex logics.”
Another interesting discovery is that the most recent change made to the C&C source code was done on May 18, 2012.
Even more interesting is the fact that Flame isn’t the only piece of malware that relies on this platform, the others – currently unknown - being named SP, SPE and IP. These malicious elements are just as interesting, especially IP since it’s the most recent.
SPE is just as interesting because it’s believed that it’s currently in the wild.
Of the three communication protocols handled by the C&C - OldProtocol, OldProtocolE, SignupProtocol – Flame utilizes the first one. A new protocol – Red Protocol - is currently being developed, which indicates that the code is (or at least it was, recently) still improved.
Researchers found that the programmers who created the platform have been trying to make something that appears to be a legitimate CMS platform.
“The stolen data is encrypted on the server in such a way that only the attackers can read it, through strong public key cryptography. These features are not normally found in malware created by everyday cyber-criminals, reaffirming our initial conclusions that Flame is a nation-state sponsored attack,” Kaspersky experts explained.
 14 DAY TRIAL //
14 DAY TRIAL //