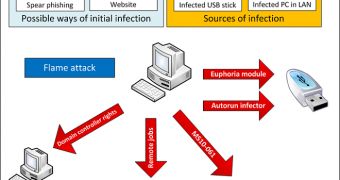
There are a couple of new reports about the now-infamous Flame that we thought of sharing with our readers. One group of researchers has stated that the malware may have been developed by world-class experts, while Symantec has revealed that the threat comes with a “suicide” functionality.
While analyzing Flame (or Flamer, as they call it) last week, researchers from Symantec noticed that, at one point, some of the malware’s remaining command and control (C&C) servers started sending an updated command to compromised computers.
“Following the request, the C&C server shipped them a file named browse32.ocx. This file can be summarized as the module responsible for removing Flamer from the compromised computer. One could also call it the ‘uninstaller’,” they explained.
The browse32.ocx module contains a list of files and folders utilized by Flame and removes all of them. Then, it overwrites the disk with random characters to ensure that no information can be recovered.
The particular module analyzed by Symantec was created on May 9, 2012, but experts believe that older variants may have been utilized in the past.
However, an interesting fact is that Flame comes with a SUICIDE component that has the same functionality as the browse32.ocx module. It’s uncertain why the cybercriminals preferred to use the module instead of the component.
Getting to the second interesting discovery, yesterday we learned that the Flame used an unknown md5 chosen-prefix collision attack.
Marc Stevens, a cryptanalyst famous for breaking the MD5 hash function for https security in 2008, and his team from CWI in Amsterdam have been studying these attacks and they believe that highly trained researchers would be needed to develop this design.
“Flame uses a completely new variant of a ‘chosen prefix collision attack’ to impersonate a legitimate security update from Microsoft. The design of this new variant required world-class cryptanalysis. It is very important to invest in cryptographic research, to continue to be ahead of these developments in practice,” Stevens explained.
 14 DAY TRIAL //
14 DAY TRIAL //