A cyber espionage group believed to be launching intelligence gathering campaigns since 2009 has been found to leverage a previously unknown vulnerability affecting desktop versions of Windows starting with Vista and server editions 2008 and 2012.
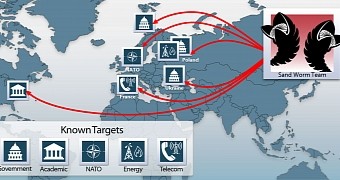
The zero-day, which allowed execution of arbitrary code, is now tracked as CVE-2014-4114 and was used to target NATO, government organizations in Ukraine and Western Europe, as well as companies in the telecommunications and energy sectors.
Patch for the vulnerability is ready
The vulnerability used by Sandworm allows the attackers to deliver a weaponized PowerPoint document to the victims, which would download a variant of BlackEnergy malware. Spear-phishing was the vector the group relied on.
iSight says that the glitch is present “because Windows allows the OLE packager (packager .dll) to download and execute INF files.”
Applied to the observed attacks, the packagers permit a Packaged OLE object to point to external files from an untrusted source. This results in downloading the executable items and running them with specific commands.
“An attacker can exploit this vulnerability to execute arbitrary code but will need a specifically crafted file and use social engineering methods (observed in this campaign) to convince a user to open it,” iSight writes.
The security company disclosed the details of the glitch to Microsoft and the two entities collaborated for addressing the problem.
As a result of this, a patch has been developed and it will be delivered to Windows users through the monthly updates provided by Microsoft, commonly known as Patch Tuesday.
Apart from this vulnerability, Sandworm relied on other flaws, non-zero day, to carry out its activity.
Russia is believed to be the culprit
Security researchers at iSight Partners discovered the security flaw in the wild and connected the dots between the recent attacks and older incidents based on the analysis of the code.
The many references in the malware to the science fiction classic Dune made the researchers give the cyber espionage group the name “Sandworm.”
Some of these references are present in the URLs for some command and control (C&C) servers that have been used for other campaigns in the past, spanning as far as 2008. This led iSight to the conclusion that the same organization was orchestrating the attacks.
The fact that the files on the C&C servers were written in Russian made the researchers link the group to Russia.
This alone would make the conclusion pure speculation, but more evidence is provided by the information the victims were baited with, which touches on operations aimed against Russia.
 14 DAY TRIAL //
14 DAY TRIAL //