A highly advanced cyber-espionage group dubbed Equation has been modifying the firmware in more than a dozen hard drives, possibly infecting tens of thousands of computers in sensitive sectors of activity worldwide.
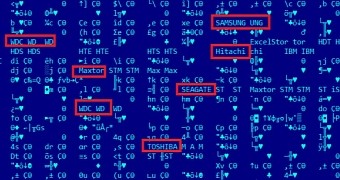
The list of storage units that have been tampered with includes devices manufactured by Seagate, Western Digital, Toshiba, Maxtor, Toshiba, Micron, Samsung and IBM.
Threat actor creates hidden persistent storage on the HDD
Among the tools used by the malicious actor is a module named “nls_933w.dll,” whose purpose is “to reprogram the hard drive firmware of over a dozen different hard drive brands.”
Kaspersky says that this module is probably the most powerful one used by the group and it represents a technical achievement that proves the sophistication level of the group’s abilities.
By planting the infection in the firmware of the hard drive, Equation ensured persistence on the machine until the tampered storage would be replaced, since wiping the hard disk and/or re-installing the operating system would have no effect and the infection would re-occur.
The researchers caught two malicious modules that could reprogram the HDD firmware, one of them, compiled in 2013 and found in GrayFish malicious platform, being able to affect no less than 12 brands.
The first version was detected in EquationDrug platform and researchers found a compilation date from 2010. It affected a total of six HDD brands.
Reprogramming the firmware of the storage devices allowed the threat actor to create a hidden data storage space isolated from the operating system and which could be accessed only through specific methods created by the threat actor.
A former intelligence operative told Reuters that the NSA developed a method to hide malware in hard drives.
The affected units are used by government and diplomatic institutions, telecommunication companies, organizations activating in fields such as aerospace, energy, nuclear research, oil and gas, military, nanotechnology, transportation, financial sector, or entities developing encryption technologies.
Equation and Stuxnet may be one and the same group
Security researchers found evidence that the Equation group relied on malware pieces compiled in 2002, although the command and control (C&C) server used for transmitting the data was registered in 2001. However, they also found that other C&Cs used by the group had been registered since 1996, suggesting that the group has been active for almost 20 years.
A total of six Trojans have been identified by the researchers (named EquationLaser, EquationDrug, DoubleFantasy, TripleFantasy, Fanny and GrayFish by Kaspersky), but their number is likely larger as others have yet to be identified.
In a blog post published on Monday, Kaspersky says that Equation has interacted with the groups behind Stuxnet and Flame, “always from a position of superiority, as they had access to exploits earlier than the others.”
The connection with the actors behind Stuxnet was discovered in the Fanny worm, detected in December 2008, tasked with mapping air-gapped systems. Fanny used two of the zero-day exploits in the tool attacking the Iranian nuclear plant at Natanz. Furthermore, Fanny spread using the LNK exploit employed in the Stuxnet attack.
Important to note is that the exploits were first incorporated in Fanny, and then observed in early versions of Stuxnet. This indicates that the Equation group had access to the security flaws before the group behind Stuxnet.
The fact that different computer worms used the same exploits at around the same time points to the conclusion that the Equation group members and the developers of Stuxnet are either the same or are working together, Kaspersky says.
Stuxnet is believed to have come into existence as part of a joint effort between the NSA, CIA and the Israeli intelligence. Kaspersky does not make any attribution in its analysis but does share details that point to tools included in a leaked catalog with utilities used by the NSA.
 14 DAY TRIAL //
14 DAY TRIAL //