It's starting to look like browser makers should just block all Java versions and then whitelist the ones that aren't vulnerable rather than just keep adding more and more to their blocklist.
Yet another Java exploit is out in the wild with no patch from Oracle leaving browser and OS makers scurrying to fix it in whatever way possible.
The exploit affects the latest Java 7 Update 10, so there's no getting away from it except turning off Java altogether, which you should probably do anyway, or being really careful about the sites you visit, which isn't as smart as you'd first think.
"There is no patch currently available for this issue from Oracle. To protect Firefox users we have enabled Click To Play for recent versions of Java on all platforms (Java 7u9, 7u10, 6u37, 6u38)," Mozilla explained.
"Firefox users with older versions of Java are already protected by existing plugin blocking or Click To Play defenses," it added.
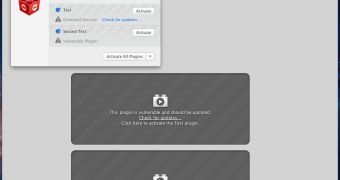
With click-to-play, Firefox got a simple and very effective mechanism from keeping plugins from running all the time.
With click-to-play enabled, plugins and content that relies on them are only loaded on demand when the user needs them. It's probably a good idea to have click-to-play enabled for all plugins all the time.
Blocking vulnerable plugins with click-to-play also has the advantage of keeping users protected while also allowing them to use the plugin if they absolutely must.
There are cases when plugins, even Java, is needed and some users simply can't disable or uninstall it. For them, the option was to leave Java running and hope for the best.
With click-to-play, they are protected from drive-by attacks, i.e. those happening with no input from the user except visiting an infected site, but can still use Java when they need it on the sites they trust.
 14 DAY TRIAL //
14 DAY TRIAL //