Security patches for Android OS are not delivered at the same time for all users because their implementation often depends on third-parties, carriers and/or phone manufacturers. In the meantime, there is a simple way to check if the device is affected by some of the vulnerabilities.
Bluebox Security Scanner can currently detect if the device has been patched against four Android bugs, and in some cases it can provide contact information for the entity responsible for delivering the fixes.
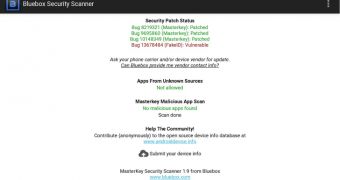
At the moment, the tool, free on Google Play, determines if bugs 8219321, 9695860, 10145349 and 13678484 have been eliminated. All of them refer to the verification process of the digital certificate for each app installed on the system.
Patches have been released for all of them, but for the aforementioned reasons, not all of them reached Android users.
The new tool can also check if apps leveraging one of the first three bugs (Master Key) take advantage of the phone’s system.
However, more importantly, the latest version of the scanner is able to detect if the patch for the latest Android OS critical vulnerability is installed. Dubbed FakeID by Bluebox Security, this flaw has the potential to compromise an Android phone completely, on operating system versions lower than 4.4 (KitKat).
The security glitch is caused by the fact that the Android packager does not carry out any verification of the legitimacy of a digital certificate chain, which allows a potential attacker to create a signature for an app and claim it to be issued by a trusted developer.
By doing so, an app could be awarded the same privileges as those the software from the trusted developer benefits from.
Google has provided a fix for the FakeID flaw, and it is now up to the device manufacturers to integrate it in the firmware and distribute the update.
Bluebox’s scanner utility can also inform the user if the installation of apps from unknown sources is enabled on the device.
Inherent Android problems aside, adding software from alternative, unverified app repositories is the top cause of malware infection on the operating system.
Users are often deceived to install rogue apps posing as legitimate ones, exposing them to various risks. Cybercriminals can use malicious APKs to collect information relating to bank accounts or private data, such as text messages, contact and phone call lists, details about the apps installed, and stored files.
Recent Android malware can encrypt specific data on the device and ask for a ransom fee in order to decrypt it.
 14 DAY TRIAL //
14 DAY TRIAL //