Cybercriminals believed to be from Russia have been observed to rely on fileless ransomware sent to unsuspecting users by abusing an ad-bidding network to win an ad spot on popular websites.
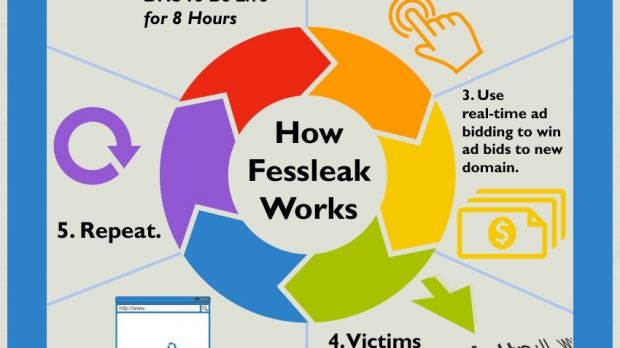
Security researchers say that the cybercriminals would first set up a short-lived burner domain directing to a landing page where the payload was hosted. Then they would engage in real-time bidding for ads pointing to the burner domain.
No malicious file is dropped on the computer
Once their bad ad found its place on a popular website and users clicked on it, they would be redirected to the malicious domain and then to the final landing page.
After eight hours, which was the time set for the DNS to be active on the burner domain, the campaign would expire and the entire cycle would be repeated with another burner.
Researchers at Invincea observed that the malicious file received by the users was not dropped on the storage unit of the system; instead, it would be extracted directly in the memory of the system using the “extrac32.exe” tool in Windows.
It appears that the ransomware comes with protection against virtual environments, which are often used by security researchers when doing malware analysis.
Unless a protected space is detected, the threat starts the data encryption process ending with the display of a ransom note for the unlock key.
They say that this operation was linked to dozens of domains, all registered by someone using the email address “[email protected],” which is also the reason they named the attack Fessleak.
Cybercriminals switch from fileless to zero-day exploits
Invincea says that when the recent zero-day exploits (CVE-2015-0310, CVE-2015-0311 and CVE-2015-0313) for Flash Player appeared, the Fessleak group stopped using the fileless method and focused on the delivery of the malware using the more traditional Flash exploitation methods.
“Now Fessleak drops a temp file via Flash and makes calls to icacls.exe, the file that sets permissions on folders and files. At this time, there is no detection for the malicious binary, which likely rotates its hash value to avoid AV detection,” the researchers said in a blog post on Wednesday.
The list of websites displaying the bad ads includes HuffingtonPost.com, RT.com, Photobucket.com, CBSsports.com, HowtoGeek.com, Fark.com, Thesaurus.com, and Match.com.
Invincea has been tracking this threat actor for a long time and their logs show that the activity of Fessleak started at least on October 17, 2014 and continued through 2015, the latest recording of an attack being on February 3, 2015, on Thebrofessional.net.
 14 DAY TRIAL //
14 DAY TRIAL //