Members of the Syrian opposition have been lured by hackers to engage in conversations over Skype with a fake individual masquerading as a beautiful female showing support for their cause.
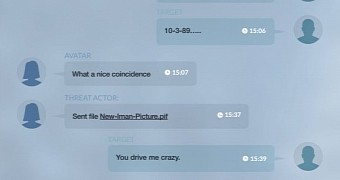
By tricking them into a photo exchange, the hackers would deliver a self-extracting RAR file that was renamed with the PIF (Program Information File) extension. This type of file is not an executable, but it would run the data inside.
Military, political and humanitarian data exfiltrated
Once opened, the photo of the “femme fatale” would be launched along with malware included in the package.
Security researchers at FireEye found that the hackers used DarkComet RAT (remote access Trojan) to gain complete access to the compromised systems. They observed that the malware would be dropped via a custom tool (BLACKSTAR), which makes detection more difficult.
It appears that the data exfiltrated, tallied at some 7.7GB, included 64 Skype account databases, 31,107 conversations, 12,356 contacts, and 240,381 messages.
Hackers were very careful with what they stole and only in a few cases was data that did not fit their purpose downloaded.
The information stolen related to military operations (annotated satellite images and battle plans were found), political strategies and humanitarian needs assessments; it also contained personal details about refugees, as well as documents and strategy data from media releases, situation reports, and lists of casualties.
FireEye says that the victims fit the profile of an opposition leader, a defector, a humanitarian, and a media activist. In all cases, they played important roles in the organization.
Small set of targets, large cache of data
Under the “femme fatale” guise, the hackers would obtain precious information about the targets. Among the first questions seems to be the type of computing device the victim uses, probably in order to deliver malware compatible with the platform.
“The other personal questions presumably helped the threat actors systematically collect information from each of their targets. The threat actors would sometimes reinitiate chat sessions with victims after a period of inactivity to collect additional details,” FireEye says in a report.
The researchers allege that the threat group probably gathered a large cache of details by breaching a small number of systems, on account of the fact that the Syrian opposition shared the computers for satellite-based Internet access.
It appears that the hackers relied on a command and control server outside Syria, unlike other threat actors whose attacks had been previously documented by other security companies.
“In addition, the activity does not share any of the tactics or tools with activity profiled in another recently released report on potentially ISIS-linked malware in Syria,” researchers found.
 14 DAY TRIAL //
14 DAY TRIAL //