Fanny worm, the malware piece that preceded Stuxnet in methods used for infection and propagation from one machine to another, has been publicly available for download since July 13, 2010.
Designed for USB drives, the worm is the creation of Equation, the name given by Kaspersky researchers to the most sophisticated cyberespionage group seen to date, and it was discovered to have a compilation date from mid-2008.
When analyzing the toolset used by the Equation group, researchers’ attention lingered on Fanny because of its evident ties to Stuxnet due to relying on the same exploit affecting LNK files in Windows.
Stuxnet is the malware that targeted the Siemens SIMATIC Step 7 software or SIMATIC WinCC program used in industrial control systems (ICS) at uranium enrichment plants outside Natanz, Iran.
Forum user posts link to Fanny worm download
Although Kaspersky found the trail of the Equation group in early 2014 and started analyzing its tools and methods, Fanny worm has been sitting in plain sight, ready to be dissected, on a Malaysian forum that is ranked 17 in the country, according to data from Alexa.
A user posted a cry for help regarding a virus that launched itself from a USB drive on a Windows system with all patches available and with autorun or autoplay functionality disabled.
“You insert the USB thumbdrive, the computer gets infected. Even when the patches has been applied, and autorun and autoplay has been turned off. The weirdest thing of all is, there is in fact no autorun.inf on the root of the infected USB drive,” an individual posting under the name “dkk” says on the forum.
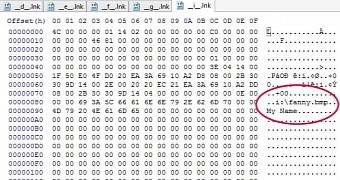
He then explains that a set of LNK files were available on the removable storage device, along with a file called “fanny.bmp,” which Kaspersky uncovered to be used for self-replication.
Answer received almost five years later
Dkk’s description almost five years ago of how the malware operates and how the computer gets infected is the same as the one provided by Kaspersky this week, when researchers presented their results of the analysis of the Fanny worm.
The compromise would occur the moment the contents of an infected USB drive were accessed with a file manager.
What the forum poster did not know was that the purpose of the LNK files was to launch “fanny.bmp” if available in the root of any drive from D:\ through J:\. However, he was able to determine that the presence of mscorwin.dll under the “system32” folder indicated an infection, a detail also pointed out by Kaspersky.
Unfortunately, dkk’s brief analysis of the infection and an advise on how to deal with the issue remained unanswered until today, when multiple users hurried with replies saying that the post was famous.
An analysis on VirusTotal shows that most of the antivirus products (48/57) enlisted to the service are capable of detecting Fanny worm.
 14 DAY TRIAL //
14 DAY TRIAL // 
