Security experts from Websense have spotted a few interesting spam campaigns designed to distribute a variant of Zbot, the notorious malware that’s used by cybercriminals to steal banking credentials and other personal information.
One of the spam campaigns leverages the name of Wells Fargo. The emails urge recipients to open an attachment which hides a piece of malware.
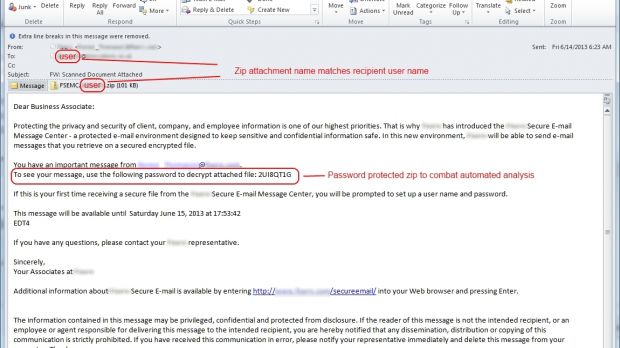
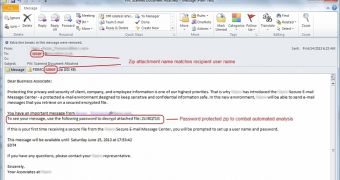
What’s interesting about these emails is that the name of the attachment is custom generated to match the intended recipient’s email username. This tactic makes the malicious message more legitimate-looking and increases the campaign’s chances of success.
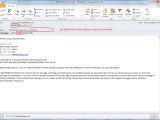
The second spam campaign relies on fake Trusteer emails to distribute malware. Recipients of these emails are advised to update their Trusteer products by using the attached file.
Similar to the bogus Wells Fargo emails, the name of the attachment matches the username of the recipient.
An older campaign that was doing the rounds in mid-June employed an extra trick, besides the custom attachment names. The attachment was a password-protected archive file, for which the password was included in the body of the email.
This technique increases the chances for the malicious emails to bypass security solutions.
Check out the gallery to see what these emails look like.
 14 DAY TRIAL //
14 DAY TRIAL //