Emails circulating recently claim to inform of a pricey purchase in order to make users access malware stored in Dropbox cloud.
Legitimate cloud storage services are used more frequently by cybercriminals to deliver threats to unsuspecting users. By doing this, they can hide their identity and suffer no damage when the account is terminated.
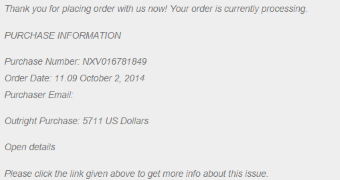
The email contains a link to a Dropbox account that delivers a malicious file. Most of the users should be able to spot the deceit, but others have the highest chances of falling into the trap.
Crooks use simple but efficient social engineering
The text is carefully crafted to create a sense of urgency in accessing the file referred to in the message, which actually deploys the threat.
Several samples of the malicious email have been caught by Online Threat Alerts, all built after the same pattern. To make it more believable, the crooks provide the email address of the victim in the message. This may seem like nothing much, but it is an efficient approach in many observed cases.
Cybercriminals creating these false messages are known to be experienced in social engineering tactics and in this particular example the bait used consists in a bill for a large purchase, determining the user to check for detailed information in the provided document.
Once the link is accessed, a file that appears to contain the order information is downloaded, which is in fact a Trojan or a malware dropper.
Dropbox has taken the necessary measures to remove the dangerous file from their infrastructure and at the moment the URL generates the 460 error specific to unavailable content.
Malware could be intended for various criminal activities
There is no information about the type of the threat, but it could be anything from an info-stealer designed to exfiltrate sensitive data to backdoors into the system.
Other nefarious purposes it could be intended for include DDoS (distributed denial-of service) attacks, mining for digital currency, scanning websites for vulnerabilities or checking other computers for specific ports that are open and known to belong to certain services targeted by the attacker.
There have been cases where a botnet was used to look for machines with remote control software installed, which is often used on payment processing systems.
Cybercriminals often deploy malware with a wide set of capabilities in order to create large botnets that are then rented for other crooks to conduct their activities.
Running targeted DDoS attacks can be done for a few hundred dollars these days, depending on the number of computers in the botnet.
Users are advised to exercise care when dealing with unsolicited emails and messages coming from individuals or services unknown to the recipient.
 14 DAY TRIAL //
14 DAY TRIAL //