After masquerading rogue antivirus as Microsoft Security Essentials and a range of additional genuine security solutions, cybercriminals are even copying the Microsoft Update site with the latest fake AV attack targeted at users of Firefox on Windows.
Chester Wisniewski, a Senior Security Advisor at Sophos Canada is warning of the new “distribution model” of a fake antivirus which attempts to fool customers into thinking they’re actually downloading and installing a security solution from Microsoft Update.
The attack originates from a source that is distributing fake AV, targeting Windows users, both those running Internet Explorer and Firefox.
A previous attack from the same cybercriminals involved fake security alerts provided inside Firefox. This time around, they’re trying to spread a rogue AV through a fake Microsoft Update site.
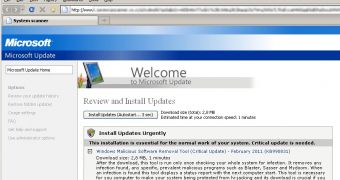
“The page is nearly an exact replica of the real Microsoft Update page with one major exception... It only comes up when surfing from Firefox on Windows,” Wisniewski explained.
“The same site was also hosting the traditional Windows XP explorer scanner we have seen for years, as well as a new Windows 7 scanner.”
Attackers never seem to be in short supply of social engineering schemes designed to get unsuspecting users to infect their computers with malicious code.
And this is nothing but another social engineering scheme. Users should keep in mind that the real Microsoft Update site only works with internet Explorer and not with Firefox.
In this particular attack, victims are urged to install the fake updates urgently, with attackers claiming that “This installation is essential for the normal work of your system. Critical update is needed.”
Users can see a screenshot of the social engineering attempt above, and they must remember not to trust a System Scanner that’s being offered to them out of the blue, especially from Microsoft Update and when they’re surfing the web with Firefox.
Here is the message enticing them to download the fake AV and infect their machine, the spelling errors are that of the original authors:
“After the download, this tool is run only once checking your whole system for infection. It removes any infection found, any specific, prevalent malicious programs such as Blaster, Sasser and Mydoom. When an infection is found this tool displays a status report with the next computer start. This tool is necessary for you computer to make your system being protected from hi-jacking and its download is crucial if you value your personal data and your privacy.”
Obviously, victims that allow themselves to be tricked into downloading this fake AV will end up infecting their computer instead of getting the benefits of the Windows Malicious Software Removal Tool, which is a genuine product from Microsoft.
 14 DAY TRIAL //
14 DAY TRIAL //