An extension from Google Chrome purporting to deliver Adobe’s Flash Player has been found to launch a website apparently built for click fraud, triggered by opening Facebook or Twitter.
The entire process is quite complex, because it involves downloading multiple files on the computer and bypasses the recent protection added to Chrome against installation of browser extensions that are not in Chrome Web Store.
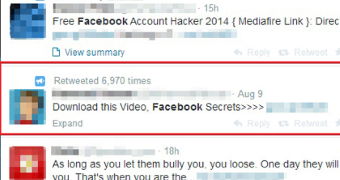
It all starts with a baiting tweet that advertises “Facebook Secrets”, claiming to show videos that are not publicly available, and offers a shortened link for getting it.
The downloaded file is a malware dropper with the name “download-video.exe”, says fraud analyst Sylvia Lascano of Trend Micro, detected by the security firm’s products as TROJ_DLOADE.DND.
It is used to funnel additional malware into the system, a Chrome browser extension which masquerades as Flash Player being among them. This could be used for more aggressive threats designed to steal credentials for online services.
“In order to bypass Google’s security policy, the malware will create a folder in Google Chrome’s directory where it will be drop browser extension components,” writes Lascano in a blog post.
The extension manifest and the script (“crx-to-exe-convert.txt”) that needs to be loaded are added to Chrome’s extension folder. After all the data is parsed by the browser, the extension is ready to work.
Although Google implemented a security measure against browser components outside the Web Store in order to eliminate risks for the users, these can still be temporarily installed manually.
As soon as the browser is restarted, however, the pieces not complying with the policy are automatically booted from Chrome and the entire process of manual installation needs to be repeated.
We contacted Trend Micro for more information about the bypass of the security gate in Chrome, but a reply has yet to be received.
Lascano says that the extension sits quietly in the browser until Facebook or Twitter websites are loaded. That’s when it kicks in and launches in the background a site in Turkish.
“The site is written in Turkish and phrases such as ‘bitter words,’ ‘heavy lyrics,’ ‘meaningful lyrics,’ ‘love messages,’ and ‘love lyrics’ appear on the page. This routine could be a part of a click fraud or redirection scheme,” the analyst says.
It appears that the tweets promoting the initial malware dropper benefited from wide distribution, as they had been shared more than 6,000 times by the time they were discovered.
The fact that the link was shortened, hence users do not have visibility of where it directs, coupled with the promise to reveal secrets, contributes to spreading the campaign.
The advice for protecting your computer against this sort of threats is to refrain from accessing links from suspicious sources.
 14 DAY TRIAL //
14 DAY TRIAL //