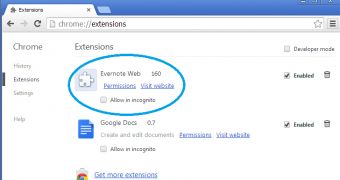
A potentially unwanted program (PUP) installs a fake Evernote that bypasses the security measures available in Chrome web browser, and starts spewing ads at the user.
The name of the extension, Evernote Web, as well as its ID, is identical with that of the real component. Moreover, it directs the user to the legitimate entry in the Chrome Web Store when clicking on the “Visit website” button. All these elements make Google Chrome believe that the real extension is installed.
Security researchers from Malwarebytes have analyzed this browser component, and found that it is digitally signed by, “Open Source Developer, Sergei Ivanovich Drozdov,” with a certificate that has been revoked by the issuer.
“This serves as another reminder that you can’t always trust a program just because it’s digitally signed,” says Joshua Cannell of Malwarebytes.
The action taken by the fake extension consists in running a content script in the context of a web page visited by the user. This results in advertisements being displayed, all leading to other unwanted programs that are probably delivering malware, and offers.
Getting rid of the rogue extension is not a complicated task. Cannell says that removing it from the Chrome extension page does the trick.
 14 DAY TRIAL //
14 DAY TRIAL //