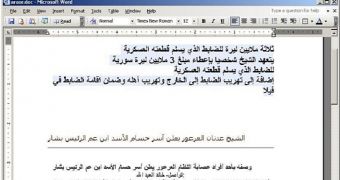
Cybercriminals continue to leverage the conflict in Syria for their operations. One campaign, which targets hotels, oil companies, and government agencies, relies on fake emails allegedly coming from Sheikh Adnan Mohammed al-Aroor, considered to be the face of the anti-government movement in Syria.
According to Symantec experts, the malicious emails carry a zip file attachment that contains a .lnk shortcut file.
When executed, a file called 1.exe is dropped onto the targeted device, creating other files and adding registry entries to ensure that it can run every time the computer is started.
While the victim sees a document containing a message from Sheikh Adnan Mohammed al-Aroor, in the background, the Xtreme Remote Administration Tool (RAT) steps into play.
Identified by Symantec as W32.Extrat, the RAT allows its master to monitor keystrokes and steal information from the infected computer.
 14 DAY TRIAL //
14 DAY TRIAL //