In the past few days we have made a couple of advisories in which we have detailed how Craigslist scams work and how fraudsters trick users. However, such schemes are not the only thing internauts should worry about, since experts have found emails allegedly coming from Craigslist that lead to the infamous Blackhole exploit kit.
Websense researchers have discovered around 150,000 malicious emails that lure recipients to compromised websites that host the exploit kit.
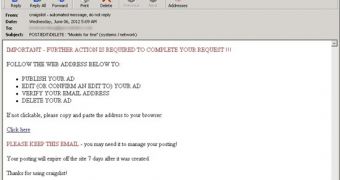
Here’s what some of the subject lines look like: POST/EDIT/DELETE : "Models for fine" (systems / network) POST/EDIT/DELETE : "Studio4PaintWorkCatskills" (education) POST/EDIT/DELETE : "Show Your Art" (cars+trucks)
The message itself is designed to look like a legitimate automated email notification, even the sender’s address being forged to appear as genuine, but the links they contain don’t point to Craigslist.
Once the link is clicked, the victim is taken to a compromised WordPress webpage that contains obfuscated JavaScript. This piece of code actually hides an iFrame redirection that takes users to a malicious website.
Here, the Blackhole exploit kit attempts to exploit Adobe Reader, Adobe Acrobat and Windows Help and Support Center vulnerabilities in order to push a piece of malware onto the victim’s device.
In these situations, the best way to tell if an email is legitimate or not is to place the mouse over the link so that the web browser or email client shows you where it points to. If it’s anything other than the official website, you can be certain that you’re dealing with a malicious plot.
However, the best way to ensure that you are protected against such threats is to keep your software updated at all times. If everything is patched up, the exploit kit will not be able to serve the malware.
 14 DAY TRIAL //
14 DAY TRIAL //