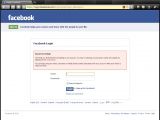
The Facebook login page generates an overly explicit error when an incorrect email is inputted, possibly allowing attackers to match stolen information to accounts.
The Register reports that Facebook's login page is still leaking sensitive information, even though the website has just reversed a login feature that exposed profile names and pictures.
When trying to authenticate on Facebook with an incorrect password, the website generates a meaningful error reading "Please re-enter your password. The password you entered is incorrect. Please try again (make sure your caps lock is off)."
However, if a user tries to login with an email that is not registered in the system, the Facebook login page says the following: "Incorrect Email. The email you entered does not belong to any account."
This last overly generous error poses a security risk, because it allows hackers to automatically generate email variations and test if they exist.
Remember that Facebook has over 500 million registered users and supports associating an account with multiple email addresses, all of which can be used to log into the system.
This type of sensitive info exposure bug has been known for years and that's why on failed login attempts most websites respond with "Username or password incorrect," without pointing out which one exactly.
Attacks levering this kind of bugs are not just theoretical. Last year in September we wrote about a large scale brute force attack involving email enumeration, which abused an Yahoo! API doing exactly the same thing as the Facebook login page does now.
Furthermore, not long ago, a security researcher from BitDefender pointed out that stolen email/password information found freely on the Internet, in unprotected cybercriminal caches or on underground forums can be matched to accounts listed in Facebook's public directory.
Since a lot of people tend to use the same password over multiple services, the Facebook login page error can be leveraged to significantly increase the accuracy of such an attack and even extends it to people who chose their profiles to be private.
Last week we reported about how a poorly implemented feature of the Facebook login system exposed profile names and associated pictures. Facebook addressed that by restricting it to previous logins from the same computer.
This means that people who try to log in from a computer they used for Facebook before, and input the wrong password, will see their profile and picture listed. We're not completely sure how this works, but it's probably based on left-over cookies.

 14 DAY TRIAL //
14 DAY TRIAL //