A new campaign has been recently deployed by cybercriminals trying to extend the Asprox network of infected computers, relying on fake email messages pointing to malicious online locations.
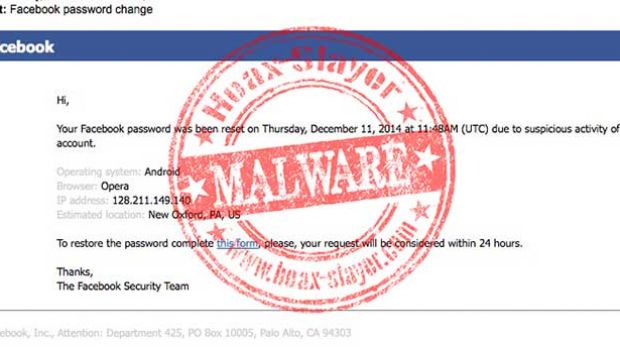
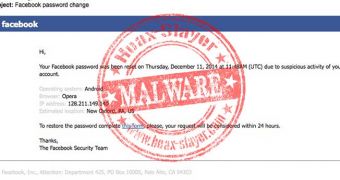
The crooks use as lure an alert that allegedly comes from Facebook, informing the recipient that their password for the social networking website has been changed.
Bogus information used as a lure
To make the communication more believable, the cybercriminals included in the email original graphics from Facebook and even a brief report of the suspicious activity that triggered the password reset action.
The report, signed by “The Facebook Security Team,” claims that an unidentified individual used Opera browser running on an Android device to access the Facebook account without authorization. A bogus IP address and its estimated geographical location are also provided.
Any geoIP search tool would show that the location in the email and the address are not a match, though. On the other hand, this clues is not likely to be picked by a regular user.
With the trap set up, the victim is offered the possibility of changing their password by accessing a given link that should load a form, where the necessary information for completing the operation should be entered.
Instead of the promised form, an archive with an executable file inside is downloaded. It appears that the compromise does not occur as soon as the EXE is launched. However, before this, a test is conducted, to check if the system it runs a version of operating system and web browser that is targeted by the cybercriminals, Hoax Slayer says.
Once compromised, the computer becomes part of the Asprox botnet, which is known for distributing spam and other malware.
Asprox botnet is highly resilient in its complexity
Asprox, also referred to as Kuluoz, was discovered in 2008 and is rented to cybercriminals for different purposes. Campaigns for increasing the number of infected computers in its network are carried out constantly.
Its infrastructure for distributing spam and malware is known to be a complex one, directing connections to specific pages, depending on the devices they originate from.
Android and iOS users land on different pages that run different types of scams through malicious apps. In the case of Windows, the latest trend is to point to malware dowloaders.
Visitors can also be directed to various adult websites, a different one for each platform, which either promote other dangerous locations or host malware.
 14 DAY TRIAL //
14 DAY TRIAL //