A developer found a way to delete any photo album on Facebook by using only four lines of code; exploiting the bug is not a complicated thing but considering its potential impact, it was deemed reasonable by the social network to reward the find with $12,500 / €11,000.
Facebook has over 1.3 billion users who upload hundreds of millions of photos on a daily basis; there's a lot of memories there. Given these figures, it’s no wonder that the company developers rushed a fix only two hours after validating the issue.
Message from server paramount in the discovery
The vulnerability was discovered by Laxman Muthiyah when he tried to delete one of his photo albums using the Graph API, integrated in all Facebook apps and used by developers to read and write user data, based on an access token.
Muthiyah used the Graph Explorer’s access token for the job but the response received by the server was that the “application does not have the capability to make this API call,” from which the developer understood that another application does have the power to complete the task.
As such, he changed the token with the one from Facebook mobile app for Android devices. This time, the response from the server was positive and the pictures were removed; it may not have been an unexpected result if Muthiyah was already logged into his account.
Key to deleting images of any Facebook user found
The developer went further with the experiment and selected a different album ID, one that belonged to a different user. Here’s when the bug became visible because the action was completed successfully.
Basically, Muthiyah found a way to remove any image in an album on Facebook, regardless of the user account the items belonged to.
Carrying out the task manually may be time consuming, and Facebook probably has adequate protection in place to protect various types of abuse originating from the same IP address, but cybercriminals have the resources to run an attack from thousands of machines.
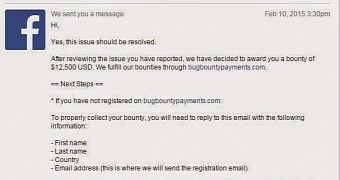
Only two hours after confirming the problem, Facebook made the necessary corrections to prevent its exploitation, according to Muthiyah.
Proof-of-concept code:
DELETE / HTTP/1.1
Host : graph.facebook.com
Content-Length: 245
access_token=
 14 DAY TRIAL //
14 DAY TRIAL //