Cybercriminals devised a clever way to steal Facebook login credentials from unsuspecting users. They designed a phishing site that urges potential victims to enter their social media credentials in order to gain access to a lot of great content related to FC Barcelona.
FC Barcelona is one of the most successful football clubs in the world, millions of people worldwide admiring its achievements and its talented players such as Lionel Messi, Carles Puyol, Gerard Pique, or Francesc Fabregas.
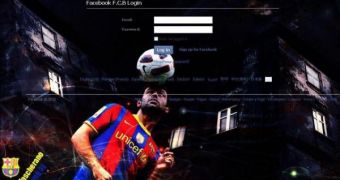
Phishers started relying on the club’s fame and created a fake website called Facebook F.C.B, which contains a picture of one of the players and the organization’s official logo, Symantec reports.
The middle of the webpage displays a couple of textboxes where a Facebook username and a password can be entered.
Once the unsuspecting user enters his credentials, he is automatically redirected to the official FC Barcelona Facebook page. Of course, at this point the sensitive data is already stored safely in a database controlled by the crooks, the redirect to the legitimate page being made with the purpose of creating the illusion of a valid login.
The chances for an Internet user to end up on this, or any other phishing site, without any interaction are slim. This is why internauts are advised never to click on suspicious links found in unsolicited emails or posts from social media sites.
They are also recommended never to provide sensitive information in response to an email or a site that's advertised by using aggressive marketing methods.
Whenever providing private data, users must ensure that the webpage they are currently on is protected by the SSL padlock and an HTTPS connection.
Those who have already fallen victim to this scam can avoid losing their Facebook accounts by immediately changing their passwords to a strong one.
Symantec informs that the malicious domain is no longer active, but since it was hosted on a free domain in the first place, it wouldn't be too difficult for the phishers to restore it in another location.
 14 DAY TRIAL //
14 DAY TRIAL //