Back in February, security experts identified several maliciously crafted Word documents being utilized by cybercriminals to target Uyghur users who had Microsoft Office installed on their Mac computers. Now, F-Secure has identified a new document.
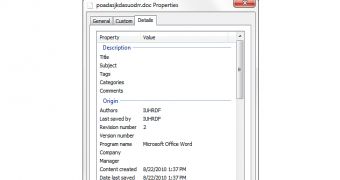
The previously identified documents listed “Captain” as being the author, but the new variant’s author is IUHRDF (International Uyghur Human Rights & Democracy Foundation).
F-Secure says that the malicious payload is the same. Only the file names and the command and control server – which is now “alma.apple.cloudns.org” – have been changed.
Once the malware infects a Mac computer, it creates a copy of itself and a launch point.
The threat is detected by F-Secure products as Backdoor:OSX/CallMe.A, the same as the variant identified back in February.
Another noteworthy thing is that the cybercriminals that target Uyghur users have started aiming at other platforms as well. In March, experts identified an Android Trojan that was being utilized against Tibetan and Uyghur activists.
 14 DAY TRIAL //
14 DAY TRIAL //