Facebook users are targeted by attacks that exploit a same origin policy (SOP) flaw in the web browser of the Android OS lower than 4.4.
The same origin policy is designed to prevent pages from loading code that is not part of their own resource, ensuring that no third-party can plant code without the authorization of the owner of the page.
Attackers can take complete control of Facebook accounts
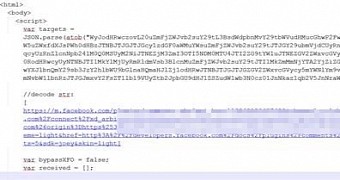
The attackers rely on the vulnerability to serve the victims a malicious JavaScript file stored in a cloud storage account.
This is done by pointing the target to a certain Facebook page that leads to a malicious location. However, the “page contains obfuscated JavaScript code, which includes an attempt to load a Facebook URL in an inner frame. The user will only see a blank page as the page’s HTML has been set not to display anything via its div tag, while the inner frame has a size of one pixel,” says Simon Huang, mobile security engineer at Trend Micro.
The capabilities of the JavaScript code are extensive, allowing an attacker to perform different activities in the Facebook account, on behalf of the legitimate owner. They can expand the list of friends, like and follow Facebook pages, and change the list of subscriptions.
Apart from this, they have the power to authorize different apps to access information from the victim’s Facebook profile, such as list of friends, birthday information, likes and friends’ likes.
Equally important is the fact that by granting access to an app the cybercriminals can steal the authorization tokens to the victim’s profile.
BlackBerry app used to steal Facebook profile access tokens
Researchers have observed that the actors behind this campaign rely on a BlackBerry app to steal the access tokens and thus hijack Facebook accounts. By choosing the name of a trusted developer, the attack has a greater chance to remain undetected.
At the moment, Trend Micro, Facebook and BlackBerry are working together to detect the attack and prevent it from being carried out against new users.
The same origin policy crack the attackers are taking advantage of is not new, and a patch was offered by Google back in September.
However, not all users are able to upgrade their mobile phones to a version of Android or of its web browser that has this issue fixed. This is because the manufacturer of the smartphone no longer pushes the update to its customers or the device itself does not support a newer edition of the operating system.
 14 DAY TRIAL //
14 DAY TRIAL //