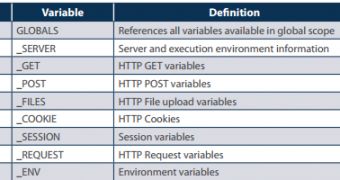
In its latest monthly trend report, IT security firm Imperva highlights the risks posed by the use of PHP SuperGlobal parameters, predefined PHP variables that don’t need to be explicitly declared.
Since PHP is highly popular, it shouldn’t surprise anyone that it’s also one of the most targeted web application development platforms by cybercriminals. That’s why, according to experts, PHP vulnerabilities deserve special attention.
When it comes to SuperGlobal parameters, Imperva believes they should be banned altogether.
During its research, the company has observed around 144 attacks per application that contained attack vectors related to SuperGlobal parameters. In fact, some of the most widely used vulnerability scanners are designed to specifically look for SuperGlobal variable manipulation.
The exploitation of PHP SuperGlobal variables, a particular case of External Variable Modification, is used for remote code execution, remove file inclusion and security filter evasion attacks.
In May 2013, a total of 3,450 requests that manipulated SuperGlobal variables were spotted. The requests came from 27 different IP addresses and targeted 24 web apps.
The attacks peaked at more than 20 hits per minute, while some of the campaigns spanned over a period of more than 5 months.
It’s also worth noting that one of the attack sources was the hijacked server of an Italian financial institution.
Besides blocking SuperGlobal parameters, Imperva makes a series of other recommendations to prevent cyberattacks.
The recommendations include the use of a positive security mechanism that specifies the allowed parameter names for each resource, and the implementation of an application layer mechanism that combines multiple systems aimed at detecting various types of violations.
In addition, Imperva recommends an “opt out” security model that can be achieved by deploying a Web Application Firewall.
 14 DAY TRIAL //
14 DAY TRIAL //