Earlier this year, researchers from Kaspersky became aware of the existence of a new banking Trojan advertised as being capable of targeting the customers of around 100 financial institutions.
One of the first posts advertising the Trojan, dubbed by Kaspersky Trojan-Banker.Win32/64.Neverquest, was published on July 18, 2013. By mid-November, thousands of attempts to infect computers from all over the world were spotted by experts.
Researchers say the relatively new threat is not being utilized to its full capacity. However, considering that it integrates self-replication mechanisms, the Trojan could spread quickly.
Neverquest is distributed with the aid of Trojan downloaders. The downloaders install a library file and make sure it’s executed automatically by creating a registry entry.
Once executed, the threat checks to see if the system is already infected. If it’s not, it phones back to its command and control server in order to retrieve its configuration file.
The configuration file contains a list of 28 websites belonging to banks and payment systems from various countries, including India, Turkey, Germany and Italy.
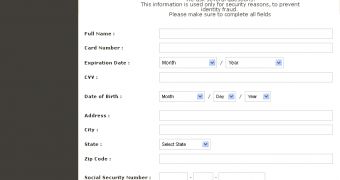
When one of these websites is visited, Neverquest injects a phishing page into the session. All the data entered on the malicious page – including name, payment card details, date of birth, social security number, password and contact information – is sent back to the attackers.
With this information at hand, the cybercriminals can conduct fraudulent transactions by using a SOCKS server and a VNC server which they employ to connect to the infected computer.
The configuration file contains a list of only 28 websites. However, the malware can be easily updated to target more.
Neverquest monitors the websites visited by users. When certain keywords are identified (e.g. balance, DepositAccounts, AccountSummary), the contents of the website and its URL are sent back to the attacker.
If the website can become a viable target, the cybercriminals make a new malicious webpage. The configuration file is then updated and distributed to all infected hosts.
Additional technical details on Neverquest are available on Kaspersky’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //