Security researchers from Trustwave’s SpiderLabs have come across a server that hosts around 2 million credentials for various online services, including websites, email, FTP accounts, Remote Desktop and Secure Shell accounts.
Most of the usernames and passwords, 1.58 million, are for websites, followed by 320,000 for email accounts, 41,000 for FTP accounts, and 3,000 each for Secure Shell and Remote Desktop.
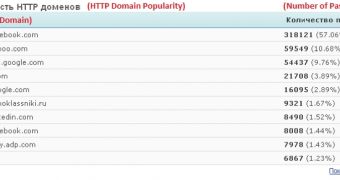
As far as the website credentials are concerned, as expected, most of them are for Facebook, Google, Yahoo, Twitter and LinkedIn. However, some of them have been stolen from the customers of the payroll service provider ADP.
The data appears to belong to Internet users from all over the world. However, because most of it has been transferred via a gateway in the Netherlands, it’s difficult to come up with precise statistics.
“Most of the entries from NL IP range are in fact a single IP address that seems to have functioned as a gateway or reverse proxy between the infected machines and the Command-and-Control server, which resides in the Netherlands as well,” SpiderLabs experts noted.
“This technique of using a reverse proxy is commonly used by attackers in order to prevent the Command-and-Control server from being discovered and shut down – outgoing traffic from an infected machine only shows a connection to the proxy server, which is easily replaceable in case it is taken down.”
Experts have taken the opportunity to analyze users’ password selection habits. They’ve found that over 15,000 of the 2 million people had used “123456.” Other popular combinations include “123456789,” “1234,” “password,” “12345,” “12345678,” “admin” and “1234.”
Over 1,200 internauts have utilized the password “1,” which indicates that there are some services that don’t enforce any type of password policy.
 14 DAY TRIAL //
14 DAY TRIAL //