Wanting to learn how many of the top 1 million Alexa websites utilize security headers to enhance protection, researchers from Veracode have set up an interesting experiment.
HTTP and HTTPS requests were sent out to the first 1 million Alexa sites in an effort to find out if they utilized X-Frame-Options, Access-Control (Cross Origin Request Sharing headers), HTTP Strict-Transport Security (HSTS) and Content Security Policy (CSP headers).
One noteworthy fact is that in case errors occurred, the response data was dropped in order to make the experiment as accurate as possible.
A total of 1,253,735 HTTP and HTTPS responses were analyzed, of which 17,692 contained security relevant headers. There were 16,109 URLs, but some of them contained multiple security headers.
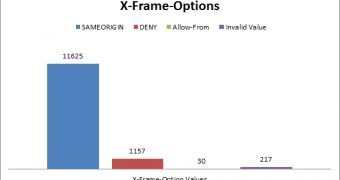
It turns out that 12,812 websites correctly utilize the X-Frame-Options header to protect themselves against clickjacking attacks. However, in some cases, the sites attempted to use a mix between the X-Frame-Options values (SAMEORIGIN, DENY and Allow-Form) causing the security benefit to become null in some browsers.
As far as Cross Origin Resource Sharing (CORS) is concerned, only 2,539 headers utilize it, 123 of which contain invalid values. CORS headers are defined when the site’s owner wants to limit how and when data is accessed by third-party origins.
When testing for HSTS – a relatively new type of header which ensures that the browser connects via HTTPS for requests going forward – 980 URLs have been found to contain a valid value.
Finally, CSP – a specification designed to limit the impact of cross-site scripting (XSS) attacks – is utilized by only 79 URLs, 32 of which include eval-script and inline-script options which significantly reduce the level of protection.
“Time and time again I was surprised at how many of the security headers were incorrectly specified,” Veracode’s Isaac Dawson, the author of the study, explained.
“Making security decisions is never a task one should take lightly, depending on the organization it could even be a time consuming affair to get a simple header added to a particular resource. To do it incorrectly is just a waste of time.”
 14 DAY TRIAL //
14 DAY TRIAL //