Researchers have been constantly analyzing the distributed denial-of-service (DDOS) attacks launched by Izz ad-Din al-Qassam Cyber Fighters against United States financial institutions but, up until now, little was known about the resources used by the hacktivists.
Incapsula, a cloud-based security and acceleration service provider, has uncovered some interesting details about the cyberattacks and the botnet that powers them after noticing that the website of a new customer was compromised.
Experts found that cybercriminals were attempting to operate a backdoor and use the site as a bot in a DDOS botnet.
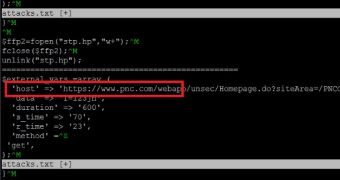
The most interesting thing is that the backdoor has been instructed to launch HTTP and UDP flood attacks against several US banks, including PNC, HSBC and Fifth Third Bank, all of which were targeted in the 4th week of Operation Ababil.
Incapsula solutions immediately mitigated the threat, so it’s uncertain how much damage has been caused, but researchers believe that an average medium-sized website could have been seriously disrupted.
One noteworthy aspect, highlighted by experts, is that the backdoor was installed on the site because its administrators used a very weak (“admin”) password.
Further analysis of the botnet and its command and control (C&C) servers revealed that the attacks were precisely timed to last between 7 minutes and one hour.
“The Botnet C&C was commanding it to work in ‘shifts’, maximizing its efficiency and ordering it to renew the attack just as the target would start to recover,” Incapsula’s Ronen Atias explained.
“During some of these ‘shifts’ the backdoor was instructed to change target and attack unrelated commercial and e-commerce sites. This all led us to believe that we were monitoring the activities of a Botnet for hire.”
Atias emphasizes the fact that the use of a “botnet for hire” is not surprising – considering that there’s a growing trend –, and neither is the fact that server machines are preferred over PC, because they have higher computing resources and they can usually access the host’s network.
As far as the attackers are concerned, Incapsula researchers have determined that they’ve been using the website of a Turkish web design company as a botnet C&C. They might have been utilizing this compromised website as a buffer between them and the target.
 14 DAY TRIAL //
14 DAY TRIAL //