It’s not uncommon for cybercriminals to register domain names similar to the ones of major companies in an effort to lure unsuspecting users into their traps. High-Tech Bridge has conducted an interesting study to find out how fraudsters are abusing domain names similar to the ones of antivirus companies.
The company has used its ImmuniWeb Phishing Monitor module to analyze 946 domains that are similar to the ones of Symantec, Kaspersky, McAfee, Avast, Bitdefender, Avira, Norton, F-Secure, G Data and Panda.
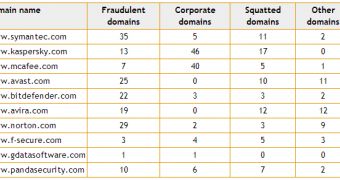
For instance, they targeted domains such as “kasperski.com,” “symanrec.com” or “mcaffee.com.” A total of 385 domains have been identified.
164 of them have been registered by individuals who want to trick users into accessing phishing websites, advertising sites, or ones that offer shady products and services.
107 of the domains identified by High-Tech have been registered by the antivirus companies in order to prevent abuse. Interestingly, 73 domains are owned by cybersquatters who hope that the IT security solutions providers will buy the names from them.
On the other hand, 41 of the domains have been registered by legitimate businesses that have similar names to the antivirus companies.
The largest number of fraudulent domains target Symantec (35), followed by the company’s Norton brand (29), Avast (25), Bitdefender (22), and Avira (19).
So which are the companies used to register the domain names? It turns out that the most popular is FABULOUS.COM, followed by GoDaddy.com, PDR, ENOM, TUCOWS, ABOVE, MONIKER ONLINE SERVICES, MarkMonitor, Internet.bs and NAMEKING.com.
Most of the websites with fraudulent content are hosted in the United States (75), Australia (24), Switzerland (19), Germany (16) and the UK (8).
“Our research clearly demonstrates that cyber criminals do not hesitate to use any opportunity to make money on domain squatting and subsequent illegal practices,” said Chief Research Officer at High-Tech Bridge, Marsel Nizamutdinov.
“There are many ways to make money from these domains: they can be resold at a profit to the legitimate owner of the Trade Mark, used to display annoying ads, redirect users to pornographic or underground pharmaceutical websites, or even to infect with malware user machines who accidentally made a typo in the URL or clicked a phishing URL.”
 14 DAY TRIAL //
14 DAY TRIAL //