The cybercriminals behind the notorious ZeuS malware continue to improve their creation. Earlier this year, experts reported an increase in the number of detections and they’ve even observed it spreading via Facebook.
However, Trend Micro experts say they’ve identified yet another spreading mechanism implemented into a new ZeuS variant.
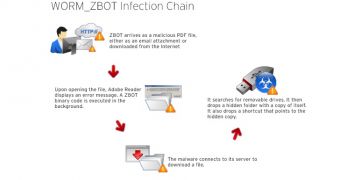
The infection starts with an innocent-looking PDF file. Once it’s opened with Adobe Reader, an exploit is triggered and the victim is notified that “extended features” have been enabled.
In the meantime, ZeuS (WORM_ZBOT.GJ) is dropped onto the system and executed. Once it finds itself on a system, the threat is capable of updating itself.
However, what’s interesting about WORM_ZBOT.GJ is the fact that it searches for removable drives, such as USB flash drives, and if one is found, the Trojan copies itself onto it. A hidden copy of the malware is placed on the USB drive, along with a shortcut file that points to it.
“This kind of propagation by ZBOT is unusual, to say the least. ZBOT malware is usually distributed by exploit kits and/or malicious attachments. This kind of behavior from ZBOT is not something we’d usually expect to see; it could mean an increase in ZBOT infections moving forward,” Trend Micro’s Abigail Pichel noted in a blog post.
 14 DAY TRIAL //
14 DAY TRIAL //