On January 31, a few weeks before the start of the world-renowned event, an RSA Conference 2014 app was published on Google Play. Experts quickly found half a dozen security issues plaguing the application.
The RSA Conference 2014 app allows users to stay up to date with activities, view the event catalogue, manage session schedules, and connect with their colleagues via a social and professional networking tool.
Security researchers from IOActive have decided to take a look at the app to see just how secure it is. In a short amount of time, they identified a total of six flaws.
The most severe of them can be exploited for man-in-the-middle (MitM) attacks. An attacker could inject a phishing page into the login sequence to trick users into handing over their credentials.
However, considering what the app is for, it’s unlikely that anyone would bother exploiting it.
As IOActive’s Gunter Ollmann puts it, “If we were dealing with a banking application, then heads would have been rolling in an engineering department, but this particular app has only been downloaded a few thousand times, and I seriously doubt that some evil hacker is going to take the time out of their day to target this one application (out of tens-of-millions) to try phish credentials to a conference.”
However, there’s another vulnerability that’s not only easy to exploit, but it could also be much more profitable.
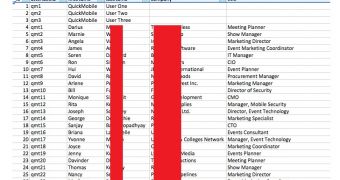
The information in the app is retrieved from an SQLite database file that’s downloaded to the smartphone. This file contains the information of every user who has signed up for the RSA Conference 2014 app, including full name, company and title.
While there are no passwords or other sensitive information in this file, marketers could probably put the information to good use.
To be fair, the application wasn’t actually developed by RSA. Instead, it was created by QuickMobile, a company that has developed similar apps for several major brands, including McDonald’s, Adobe, Kaspersky, Red Hat, and many others.
Even if RSA hasn’t developed the app, the company should have verified its security and integrity, particularly if we consider the type of business they are.
“If you're going to release your own mobile application, the security and integrity of that application are your responsibility. While you can't outsource that, you can get another organization to assess the application on your behalf,” Ollmann noted in a post published on the IOActive blog.
 14 DAY TRIAL //
14 DAY TRIAL //