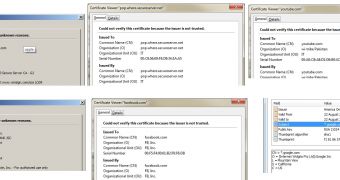
Netcraft has come across dozens of fake SSL certificates that are being used by cybercriminals to increase their malicious operations’ chances of success. The fake certificates are being leveraged to impersonate financial institutions, social networks, e-commerce websites, and even ISPs.
Experts warn that these certificates can be utilized to carry out man-in-the-middle (MITM) attacks against the customers of the targeted organizations.
While certificates alone are not enough to launch an MITM attack, they’re an important first step. For an attack to be successful, cybercriminals must also find a way to connect to the victim’s network. This task is often achieved with the aid of rogue wireless access points.
Netcraft has identified a fake facebook.com certificate served from a server in Ukraine, and a google.com certificate from a device in Romania. Fake SSL certificates for Russian organizations such as iQBank and payment processor QIWI have also been spotted.
Customers of Apple and YouTube are also targeted. However, cybercriminals have also set their sights on GoDaddy’s POP mail server.
“In this case, the opportunities could be criminal (capturing mail credentials, issuing password resets, stealing sensitive data) or even state spying, although it is unexpected to see such a certificate being offered via a website,” Netcraft’s Paul Mutton explained in a blog post.
“Although the actual intentions are unknown, it is worth noting that many mail clients allow certificate errors to be ignored either temporarily or permanently, and some users may be accustomed to dismissing such warnings.”
Commenting on Netcraft’s findings, Kevin Bocek, VP of security strategy and threat intelligence at Venafi, said, “Cybercriminals are moving faster than we think to weaponize the core element of trust on the Internet: digital certificates. The many fake certificates identified by Netcraft are just the tip of the iceberg. Cybercriminals are ramping their attacks on trust because the results are so powerful.”
“Already over a quarter of Android malware are enabled by compromised certificates and there are hundreds of trojans infecting millions of computers designed to steal keys and certificates for resale and criminal use. Today a stolen certificate is worth over 500 times more than a credit card or personal identity,” Bocek has told Softpedia in an emailed statement.
“By attacking the trust established by digital certificates, cybercriminals aren’t making a quick hit. No, their intent is to own their target. Fake, compromised, stolen, misused, illicitly obtained certificates give cybercriminals the power to impersonate, surveil, and monitor—and to do so undetected.”
 14 DAY TRIAL //
14 DAY TRIAL //