Security researchers have developed a USB dropper/spreader that’s capable of bypassing all of the popular commercial antivirus products utilized by internauts worldwide.
The antivirus programs that exist today are designed to identify threats either based on their signatures, or on their behavior. Normally, if the malware gets by one system, the other one should catch it in no time.
However, researchers have demonstrated that there is a way to create malicious elements that can spread from one computer to the other without being detected.
Soufiane Tahiri – a security researcher specialized in reverse engineering and software security – has created a virus whose behavior isn’t catalogued by any antivirus solution as being malicious.
The purpose of this test malware was to copy a presumably malicious file to a USB drive and create an autorun.inf file on the targeted device without being detected.
The “malicious element” would constantly be searching for the presence of removable disks. If one is found, it would be scanned to determine if it’s already infected.
If it’s not, the autorun.inf file and a malicious executable would be copied onto it.
So, how can this task be achieved without raising any red flags?
The first thing the expert did to ensure that his USB dropper would not be detected was to rename the functions that were usually utilized by malware to perform various tasks such as steal data or spy on the victim.
Then, instead of using methods that would clearly appear suspicious – such as File.Copy() and File.Delete() – the malware leverages an intermediary program that doesn’t require any privileges to execute basic commands. Namely, the Windows CMD command line.
“By invoking the Windows command silently, we can do everything that could be done via the command line without any restrictions!” Tahiri explained.
“We can make a thread that creates the autorun.inf file temporarily somewhere in the user’s system folder and another thread that checks for the presence of plugged removable disks and makes copy tasks via hidden instances of command line.”
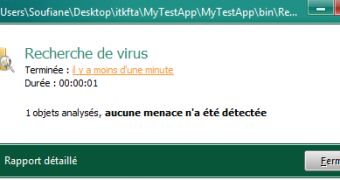
The result: a piece of software that can, in theory, cause a lot of damage while remaining undetected. The expert has tested his findings against 5 well-known antivirus applications, including BitDefender, Kaspersky and NOD32.
The researcher has told Softpedia that it’s not an easy task to make a system that would identify threats made in this manner. However, he is currently working on developing a detection mechanism.
The technical details of the research are available at itsecurity.ma.
 14 DAY TRIAL //
14 DAY TRIAL //