While attempting to study the keyloggers suspected of stealing the accounts of Diablo III players, an AVG researcher was actually confronted, in real time, by the developer of a malware.
It all started with a forum topic called “How to farm Izual in Inferno” that allegedly pointed to a video in which the method was demonstrated.
The so-called video was actually a RAR archive that contained a couple of executable files: one bearing a .txt icon and the other one a Windows Media Player icon.
Once executed, the malicious element attempted to connect to a remote server and download a new file.
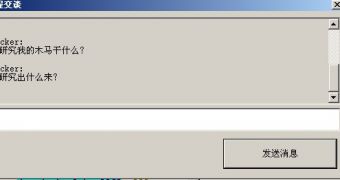
While debugging the malware, a chat dialog popped up with the message “What are you doing? Why are you researching my Trojan? What do you want from it?”
“The dialog is not from any software installed in our virtual machine. On the contrary, it’s an integrated function of the backdoor and the message is sent from the hacker who wrote the Trojan. Amazing, isn’t it? It seems that the hacker was online and he realized that we were debugging his baby,” AVG’s Hynek Blinka explained.
From the discussion the experts learned that the malware’s mastermind could actually gain access to their screen, mouse, processes, modules and even the webcam.
The attempt to dupe the cybercriminal into thinking that they were potential buyers failed, so he remotely shut down their computer.
The conclusion of the research is that this particular Trojan, BackDoor.Generic, even though it’s advertised as something for Diablo III, isn’t actually a game keylogger, but a malware designed to steal dial-up connection usernames and passwords.
For regular users the advice is obvious: steer clear of shady content served via untrusted forums. For experts: watch out, because you never know when you might be confronted by a cybercriminal.
 14 DAY TRIAL //
14 DAY TRIAL //