In June 2013, a new remote access Trojan (RAT) was made available to the public. It’s called njRAT (Backdoor.Ratenjay) and, according to experts, it’s mostly used by cybercriminal groups in the Middle East.
Symantec experts believe that njRAT is more popular in this part of the world because it’s developed and supported by Arabic speaking programmers. More precisely, the author of the RAT appears to be located in Kuwait.
Three versions of njRAT have been released so far. Although it was publicly released only in June 2013, experts have spotted a version dated November 2012, which indicates that the threat was used prior to its public launch in closed circles.
The threat spreads via USB keys and networked drives. As far as functionality is concerned, the malware can download other threats, execute commands, read and write registry keys, log keystrokes, capture screenshots and hijack webcams.
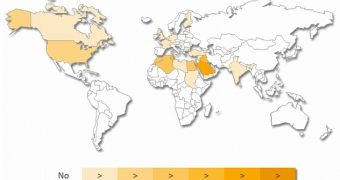
A total of 542 command and control (C&C) servers have been identified by researchers. Most of them (80%) are located in the Middle East and North Africa in countries like Saudi Arabia, Iraq, Tunisia, Egypt, Algeria, Morocco, Palestine and Libya.
A total of 24,000 computers from all over the world have been infected with the backdoor.
In addition to the C&C servers being located in the Middle Eastern region, there’s another clue which suggests that this is where most cybercriminals using njRAT are located. That’s the fact that the C&C server IP addresses are associated with ADSL lines. The author’s blog also shows that most of its visitors (over 13,000) are from Saudi Arabia.
Symantec has identified a number of websites that offer tutorials on how to use njRAT. Many of them are in Arabic.
According to experts, most of the RAT’s users are mainly interested in online pranks. However, the malware is also used to spy on governments and political activists. The EFF and Citizen Lab have discovered that njRAT is one of the tools utilized to spy on Syrian opposition groups.
A total of 487 groups have been found to use njRAT. One of them is called S.K.Y.P.E/Tagged, which hosts its C&C servers in Algeria and Egypt. These cybercriminals are distributing the threat by publishing it as a screensaver on a file sharing website.
“As large numbers of Middle Eastern attackers continue to use njRAT due to its accessibility, Symantec expects that they will try to find new ways of obfuscating the malware to evade detection by antivirus software. They are likely to continue to use njRAT since an Arabic speaking community and its Arabic author continue to provide support for the malware,” Symantec experts noted.
Additional details on njRAT are available on Symantec’s Connect blog.
 14 DAY TRIAL //
14 DAY TRIAL //