With the release of Java 7 Update 21, Oracle introduced a new system that warns users if they’re about to execute an app that hasn’t been signed with a digital certificate. However, an expert has found that the name of the app which appears in the security dialog can be easily forged.
Jerry Jongerius, the founder of Duckware, is the one who identified this and other flaws in Oracle’s Java.
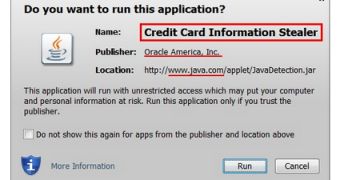
“The problem is that the ‘Name’ in this ‘security’ dialog contains an unsigned application name that can be easily forged (it comes from the unsigned web page) – at will – by anyone – a basic failure by Oracle in code signing 101 rules – only present information to the end user that was actually signed by the Publisher,” the expert noted.
Jongerius has even developed a test page which demonstrates that the application name in the Java security dialog window can be changed.
According to the expert, this demonstrates that the new Java security dialogs cannot be trusted to provide accurate information.
He admits that the risk associated with this vulnerability is low. However, a hacker could compromise an unsuspecting user’s computer simply by tricking him into running a malicious app disguised as an innocent, trusted application.
Jongerius even suggests a solution to this problem, which he claims Oracle already knows about since the test page he developed has been visited from several of the company’s IP addresses.
In addition to the name, an attacker could also change the name of the JAR file displayed in the security dialog.
“Once a Publisher signs a JAR file, there is NO legitimate reason (other than hacker activity) for Oracle to allow the JAR to be renamed to something else,” Jongerius explained.
Finally, the expert highlights the fact that Oracle’s new MANIFEST.MF “codebase” attribute, which should prevent an app from being repurposed, and the Java sandbox don’t work properly.
“What is it going to take for Oracle to take Java security seriously? Maybe the Department of Homeland Security recommending that users disable Java? No, that already happened! It is almost as if Oracle is intentionally killing off Java in the browser by ignoring security,” Jongerius concluded.
 14 DAY TRIAL //
14 DAY TRIAL //