Trend Micro Threat Researcher Kyle Wilhoit has published a report on cyberattacks against Industrial Control System (ICS), particularly SCADA (supervisory control and data acquisition) systems.
For his study, the expert set up three honeypot websites, each of them mimicking a certain type of system. Then, for a 29-day period, he observed the cyberattacks launched against them.
It’s worth noting that the results of the experiment are not based on automated attack attempts or port scans. Instead, “attack” is defined as anything that could represent a threat to the systems, including attacks against a specific protocol, unauthorized access, or modifications brought to perceived controllers.
The honeypots have been optimized and published on Google and they’ve been configured to resemble real ICS/SCADA devices.
Interestingly, the first attack was recorded just 18 hours after the honeypots had been launched. In total, 39 attacks from 14 different countries were identified.
Of the 39 attacks, 13 were repeated by the same actors and 12 of them were unique. In both cases, the attacks could be considered as being targeted.
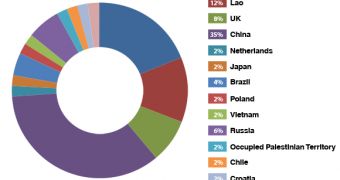
Most of the attempts originated from China (35%), followed by the United States (19%) and Lao (12%). The largest percentage of the repeat offenders came from Lao, closely followed by China.
Wilhoit found that in many of the attacks, malware exploitation attempts were made on the servers.
“Internet-facing ICS are readily targeted. Until proper ICS security is implemented, these types of attack will likely become more prevalent and advanced or destructive in the coming year,” the expert noted in the report.
“We expect attack trends to continue in the ICS arena, with possible far-reaching consequences. With continued diligence and utilizing secure computing techniques, your ability to deflect and defend against these attacks will help secure your organization,” he concluded.
 14 DAY TRIAL //
14 DAY TRIAL //