Barclay Simpson, the corporate governance recruitment company that specializes in a number of sectors, was appointed by security expert Shadab Siddiqui as being among the organizations that fail to ensure that its public website is properly protected against cybercriminals.
Barclay Simpson hasn’t responded to our inquiry, so at this point we will not publish any details of the vulnerabilities, but once the issues are addressed, we will make a proof-of-concept available.
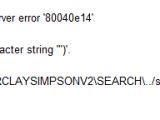
In the meantime, the screenshots provided by the researcher show the existence of SQL Injection vulnerabilities that affect the site (barclaysimpson.com).
According to Siddiqui, the security holes can be used by an attacker to execute his own malicious commands and compromise the integrity of the database, exposing all the information stored in it.
SQL Injection vulnerabilities are among the most common ones and they’re fairly easy to fix. However, as we’ve seen on numerous occasions in the past, many website admins fail to properly filter out “dangerous” characters.
Note. My Twitter account has been erroneously suspended. While this is sorted out, you can contact me via my author profile or follow me at @EduardKovacs1
 14 DAY TRIAL //
14 DAY TRIAL //