Web security analyst David Sopas from Portugal has identified DOM-based cross-site scripting (XSS) vulnerabilities on the websites of three world-renowned security solutions providers: Kaspersky Lab, Panda Security and AVG Technologies.
Security firms often warn about the importance of properly secured websites. However, these days, websites are so complex that it’s hard not to miss a few vulnerabilities.
Luckily, researchers such as David Sopas can help companies address website flaws before they’re abused by malicious actors.
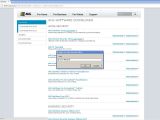
On the site of Kaspersky, the vulnerability was located on a bad validation of “location.hash” from jQuery. When the “tab” parameter of a URL was loaded, an attacker could have executed his own malicious code.
On AVG’s website, the flaw existed in the download section.
“Due to the lack of escaping/encoding the URL on the code present on file js_stdfull.js, a user could inject code into the website,” Sopas explained on his blog.
As far as Panda Security is concerned, the DOM-based XSS was located in a file called aHref.js.
The expert reported the vulnerabilities to the affected vendors as soon as they were discovered. All companies rushed to address the issues, but only Panda and Kaspersky provided feedback to Sopas.
AVG silently fixed the security hole without replying to the researcher.
“DOM based XSS is a XSS type of attack where the injected payload is executed modifying the normal environment of the victims browsers DOM instead of affecting the server side script. In other words, the HTTP response doesn't change but the client side code runs ‘differently’,” the expert told Softpedia.
“The increase of this type of attack is due to the fact present websites are using more and more use of JavaScript to power their web applications. DOM based XSS is still quite untested and that's because JavaScript is not easy to analyze under complex codes. That's part of the reason that many of the latest vulnerabilities found on Vulnerability Reward Programs are DOM XSS vulnerabilities,” he added.
“Depending on the type of vulnerability, an malicious user could use DOM XSS to steal user credentials, phishing or even to spread malware. Just like the normal XSS attacks but with a different flavor. The DOM XSS attacks are executed on the browser victim so logging this type of attacks it's very difficult.”
“This type of attack is usually easy to fix and I think it keeps reminding web developers that everything should be considered part of an attack. Sanitizing, escaping and encoding is always a good path.”
Additional technical details and proof-of-concepts are available on David Sopas’ website.

 14 DAY TRIAL //
14 DAY TRIAL //