Independent security researcher Prakhar Prasad has developed a script that’s meant to demonstrate that in many cases antivirus solutions can be highly ineffective. The expert also wants to make a contribution to the cat-and-mouse game that’s currently being played by black and white hats.
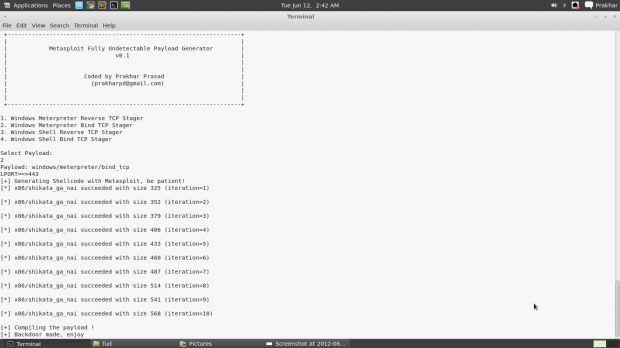
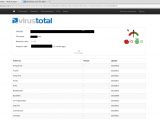
“I made a script that successfully evades AntiVirus (AV) detection for Metasploit Backdoor Payloads. All 42 AntiViruses from VirusTotal.com are bypassed,” Prasad said.
“I developed this as a part of my private research work to prove the ineffective nature of current AntiVirus technlogies to detect an existing payload or threat (Metasploit's Backdoor) if it has been repacked, obfuscated and if some Anti-Emulation technique has been employed,” he added.
The list of payloads supported by the script is this: 1. Windows Meterpreter Reverse TCP Stager 2. Windows Meterpreter Bind TCP Stager 3. Windows Shell Reverse TCP Stager 4. Windows Shell Bind TCP Stager
Prasad believes that in many cases basic antivirus software is not enough to protect internauts from the numerous threats. That’s why he recommends the use of additional firewalls, and sandboxing programs in which suspicious applications can be executed safely.
Finally, he provides a great practical example in which a cybercriminal attacks a regular internaut with the aid of a script similar to the one he developed:
Malice is a black-hat hacker uses my script to generate an undetectable Metasploit Backdoor and sends it to Bob (a common computer user), via email or any other way. By using social-engineering, tricks Bob into opening that backdoor executable.
Once Bob opens up the executable, the backdoor will establish a connection to Malice's computer. Now, Malice has the full access to Bob's computer and Malice can perform the following on Bob's computer (all this under the nose of fully updated antivirus):
1. Watch Bob's computer activities (using the out-of-band VNC that Metasploit's meterpreter provides). 2. Can sniff the traffic going in/out from Bob's computer. 3. Use Bob's computer as a proxy server (via port forwarding feature of Metasploit's meterpreter). 4. Can further pivot other computers present in Bob's network. 5. Can perform keylogging remotely (via keyscan_start feature of Meterpreter). 6. Can escalate access privileges to SYSTEM (via getsystem feature of Meterpreter).
The researcher hasn't provided the actual script because he fears that if it falls into the wrong hands it could be utilized to cause serious damage.
 14 DAY TRIAL //
14 DAY TRIAL //