More and more details are coming to light regarding the massive $45 million (€34 million) heist of which we learned after US authorities charged 8 individuals believed to be the New York cell of the criminal organization responsible for tens of thousands of illegal ATM withdrawals.
We’ve learned that the crooks most likely targeted payment processors EnStage and ElectraCard Services to gain access to bank accounts from National Bank of Ras Al Khaimah (RAKBANK) and Oman’s Bank of Muscat.
But how was the attack possible?
Few details have been provided by the authorities. However, from the Department of Justice we do know that the “cybercrime organization that used sophisticated intrusion techniques to hack into the systems of global financial institutions, steal prepaid debit card data, and eliminate withdrawal limits.”
Dodi Glenn, director of AV Labs at ThreatTrack Security, believes the hackers exploited SQL Injection vulnerabilities to penetrate the financial institutions.
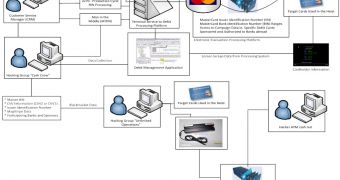
“The hackers most likely received vital bank information by compromising a customer service web portal with a SQL injection – and then most likely a keylogger and remote access tool (RAT) was used – which gave them access to the CVC or CVV data stored on the magnetic strips of prepaid credit cards,” Glenn told Softpedia in an email.
“They would have also accessed a bank identification number (BIN) database and duplicated the necessary data to access funds via a closed ATM network. They then used magnetic strip writers to put the proper account information on the backs of gift cards or hotel room keys, creating a new card that they could then use to withdraw funds from multiple ATM sites.”
ThreatTrack has also created a diagram (see screenshot) of how such attacks are carried out.
 14 DAY TRIAL //
14 DAY TRIAL //