Security researchers from Microsoft’s Malware Protection Center have identified a variant of the Exforel backdoor malware, VirTool:WinNT/Exforel.A, that’s somewhat different from other malicious elements of this kind.
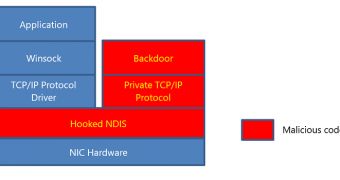
That’s because the backdoor is implemented at the Network Driver Interface Specification (NDIS) level.
Since Exforel.A implements a private TCP/IP stack and hooks NDIS_OPEN_BLOCK for the TCP/IP protocol, the backdoor TCP traffic is diverted to the private TCP/IP stack and then delivered to the backdoor.
This makes this variant of the malware more low-level and stealthy because there is no connecting or listening port. Furthermore, the backdoor traffic is invisible to user-mode applications.
According to experts, this particular version of Exforel – which can download, upload, and execute files, and rout TCP/IP packets – is used in a targeted attack against a particular organization.
 14 DAY TRIAL //
14 DAY TRIAL //