Believed to be created by two Kuwaiti and Algerian nationals, the Jenxcus (NJw0rm) and Bladabindi (NJrat) malware families focused mostly on users in Europe in the past 12 months, but they affected the United States, too.
At the moment, an accurate number of infected machines is not available, but Microsoft’s antivirus products detected different variants of the malicious items on at least 7,486,833 computers.
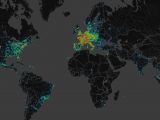
Microsoft made available a map with the global impact of the two threats, and users in Europe are the most affected. It appears that the most detections have been recorded in France, the United Kingdom, Germany, Italy, Netherlands, Belgium and Austria.
As far as the risks of an infection with Jenxcus and Bladabindi are concerned, sensitive information would be extracted from the victim’s computer and sent to remote machines under the control of cybercriminals.
The data collected consists not just of credentials for web services, as Bladabindi includes logging components and it can also control the built-in webcam to take snapshots and record without user permission. Furthermore, some variants come with remote-control capability.
They can increase in functionality and conduct more complex illegal activities by downloading other malware components from the command and control center.
The attack vectors employed by the cybercriminals are diverse and range from social engineering techniques to bundling the malicious component into programs and video files in torrent downloads.
Most of the times, cybercriminals try to lure the victim to a malicious address via email messages or posts on social networks. In some cases, the malware is purported as a Flash update that needs to be installed.
The two malware families are not new on the computer security scene, as their activity has been observed by researchers since 2012, Bladabindi making an appearance in July and Jenxcus stepping in in December.
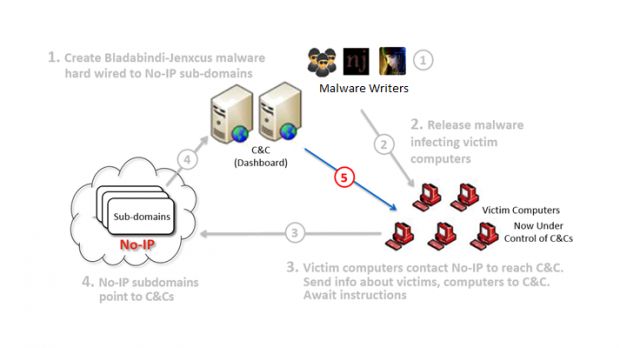
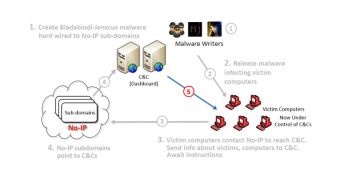
However, they managed to evade takedown action until Monday, June 30, when Microsoft seized a total of 23 No-IP domain names involved in facilitating communication between the infected machines and the command and control server of the malware.
As a result, Microsoft can identify the bad traffic and direct it to a sinkhole in order to disrupt the malicious activity.
According to a post from Microsoft, there is plenty of information online that can be used by anyone to create their variant of the threat. “This makes Bladabindi and Jenxcus a bit different from the previous botnets we have seen. A traditional botnet usually has one command-and-control (CNC) server to control all infected machines. In the case of Bladabinda and Jenxcus there can be a syndicate of botnets and thousands of botnet herders,” says the post.
 14 DAY TRIAL //
14 DAY TRIAL //